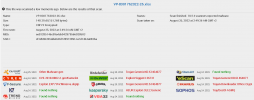
PMG use clamav as the default AV engine for virus scanning and the default detection rate is bad.
Beside add custom 3rd signature database, let try to create your own custom signature database using clamav's sigtool.
1. Use sigtool to hex dump the first 2KB output of the suspicious file to the customsign.ndb file. If the output show all 0, extract the archive file and hex-dump the content instead.
2. For html file, normalize it first before hex dump to customsign.ndb.
3. You should edit customsig.ndb and prefix the content with the appropriate Name, Type and Offset in the following format:
Name:Type:Offset:malware hex output
Such as:
Trojan.Win32.Emold.A:1:*:4d5a80000100000004001000ffff000040010000000000004000000000000000000000000000000000000000
Name is the virus name. Type is one of the following:
0 = any file
1 = Portable Executable (ie Windows exe)
2 = OLE2 component (e.g. a VBA script)
3 = HTML (normalised)
4 = Mail file
5 = Graphics
6 = ELF
7 = ASCII text file (normalised)
Offset is either * or an offset in bytes from the beginning of the file to where the hex string occurs. This is best left as * unless you know your where in the file your hex string occurs. Read the Clamav documentation if this is the case. For the virus name, I get it from virustotal.
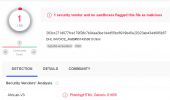
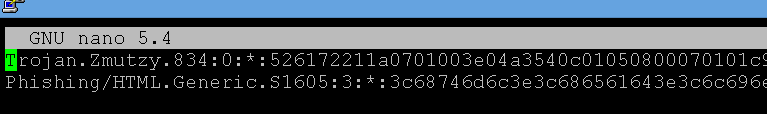
4. Let test scan the suspicious file with the customsign.ndb.
5. If successful, host the customsign.ndb file at your local web server or github public gist. Add the custom database to your /etc/pmg/templates/freshclam.cf.in.
6. Restart freshclam service with the new settings.
7. Double check freshclam have download the customsign.ndb to clamav's database directory.
8. Run a test mail with the suspicious file and clamav should block or recognize it with your custom virus name. Make sure you enable the default block virus rule.
Beside add custom 3rd signature database, let try to create your own custom signature database using clamav's sigtool.
1. Use sigtool to hex dump the first 2KB output of the suspicious file to the customsign.ndb file. If the output show all 0, extract the archive file and hex-dump the content instead.
Code:
root@pmg:~/clamav# ls
'DHL INVOICE_AWB#9514950815.html' Invoice.htm 'NOA & Pre-loading docs of CBHU9101956.docx' 'PAYMENT SWIFT COPY.r00' PO#2022CTV05-47.rar
root@pmg:~/clamav# cat PO#2022CTV05-47.rar | sigtool --hex-dump | head -c 2048 > customsign.ndb
root@pmg:~/clamav# cat customsign.ndb
526172211a0701003e04a3540c01050800070101c9dc8a8000f4b1be223102030b82dc0a0488e50b201a96cc98800b0013504f233230323243545630352d34372e6578650a03023c8c1d56e7b0d8018f83025470875553322467606877e4b24b617c04825a655016214514f0225012b68140b0f02da1290b2029e1a16d61102dcb79c3c18da16b2dc6c384c573e0f58b98f4e022bd19d61989998b88a88da86528a2a78511c0568a62c99056a97028b5277ce4a7bd6f7c90a3999ebaf9dfaefd77f477f477f3f02a92737e0d6f5bd6b7bd6f5bd6b5bdf2667e2daff09fdfdef5adeb9a9649ca43d7ab7eebf807ff4004000002683bcf1105e8208302f90e1aa6e905bfa75057fc2d6237bec3d4bda1e85ebdbec774ba7c7d675de9ea9ad454d3f7d5347a96ba6a3d56aa9d16ba5a56b5296a9ae9c7fa7b36e1aea69e929713292923311447fbbb7ed2ba0b7cbf13a79dae8e5f8908f2f2dc4cc9e7f5dc4f9957d6aad6713e55312e727c480a6734fa67660f8c45b76ca93eb98a11dfab37471a8ed9066ba497478914853384b8e727071852da446b629cb7723963fe3d6c07e9d62981e62728bcaba76c0e1060bea79ea783ff63ebe21b43486a2c99892bc53f8fc516db7ebd0fff07f114fe4c75df66251a5d6a2abfaf4d1490a4ea8c4e9db554d2626a6928d11833abeb229f72a5f1dde00d6c0d9dc4ac0c867b6eb96340b052affcc1ecb13aa8a1058aedffd85056f4e54d554989a36098c1b424d4f07fd17ba1fffebfd449f35ef3740f6b24d9a3862fbcb26da552947b9897689ca6632f9441f661837869341fe935194396a4f06750839419e2e1ca78d6e55efdb798e9b9eab40aaf696e0585b498a4e62d47a8554eb2dc535b8f181d25695ac91e59ff3cb6707c72e59f9f45013f770d410048b35fec3ea069e47421ccf13636e55f425443c66a89415abecd3f64aa4ac39d566c6d4abdbaa36682c654d67cb6427d9495a8bcee1b8115c910f5aa36b760a92add62224d53755ca0912b0f8a2a60309aac178ecb590c7f3dd7e7a1a34b0f578c0019e2b2d859158d1a205849bc5ceb7e2d45a4d1e2076ac540013eaa0273ce8601d69c560ff765204fe3ac783b6ac8681de43773b92ca152cb3b23e8afa2af3dee309cf82550aba3d14cd977bc0f600fd39f9861b57631193e1b8d3f125c6875cba4f3b1ccb9fec47239b7ff8d74cc39bc6ea0abaab289fb9a7e01abdfcf2e649aa59a8bf2f0baf1e58237a4fddcdd870116b09a09ad12924fe099feaf7e5169f81f4be5989ac2b086a7d917a77bec302ceea1a14e8990cbffb34fcf357a781310133c05fce74fa82e8621279665b703e929aa093463e6379947c274dcb1c849e4fd8d3d929572ec9fe51726ccc43c8bc5d9c8108611f4e304b0a3ea741370db5d28b91625e6114cb99b62610a7c2a9d
root@pmg:~/clamav#2. For html file, normalize it first before hex dump to customsign.ndb.
Code:
root@pmg:~/clamav# ls
'DHL INVOICE_AWB#9514950815.html' Invoice.htm 'NOA & Pre-loading docs of CBHU9101956.docx' 'PAYMENT SWIFT COPY.r00' PO#2022CTV05-47.rar
root@pmg:~/clamav# sigtool --html-normalise DHL\ INVOICE_AWB#9514950815.html
root@pmg:~/clamav# ls -all
total 1520
drwxr-xr-x 3 root root 4096 Aug 17 12:13 .
drwx------ 7 root root 4096 Aug 16 17:31 ..
-rw-r--r-- 1 root root 286708 Aug 16 09:00 'DHL INVOICE_AWB#9514950815.html'
-rw-r--r-- 1 root root 88399 Aug 16 09:02 Invoice.htm
-rw-r--r-- 1 root root 10334 Aug 16 09:06 'NOA & Pre-loading docs of CBHU9101956.docx'
-rw------- 1 root root 197021 Aug 17 12:13 nocomment.html
-rw------- 1 root root 195776 Aug 17 12:13 notags.html
-rw-r--r-- 1 root root 580074 Aug 16 09:05 'PAYMENT SWIFT COPY.r00'
-rw-r--r-- 1 root root 175788 Aug 16 08:50 PO#2022CTV05-47.rar
drwx------ 2 root root 4096 Aug 17 12:13 rfc2397
root@pmg:~/clamav# cat nocomment.html | sigtool --hex-dump | head -c 2048 > customsign.ndb
root@pmg:~/clamav# cat customsign.ndb
3c68746d6c3e3c686561643e3c6c696e6b2072656c3d2273686f72746375742069636f6e2220687265663d2268747470733a2f2f6c6f67696e63646e2e6d73617574682e6e65742f31362e3030302e32393036382e392f696d616765732f66617669636f6e2e69636f223e3c6d65746120687474702d65717569763d22636f6e74656e742d747970652220636f6e74656e743d22746578742f68746d6c3b20636861727365743d69736f2d383835392d31223e3c7469746c653e2a2a2a2a20696e20746f202a2a2a2a202a2a2a2a2a2a2a2a2a206163636f756e743c2f7469746c653e3c7374796c6520747970653d22746578742f637373223e626f64792c2068746d6c207b206865696768743a20313030253b206d617267696e3a20303b20666f6e742d66616d696c793a20227365676f6520756920776562666f6e74222c202d6170706c652d73797374656d2c202268656c766574696361206e657565222c20226c7563696461206772616e6465222c2022726f626f746f222c2022656272696d61222c20226e69726d616c61207569222c2022676164756769222c20227365676f652078626f782073796d626f6c222c20227365676f652075692073796d626f6c222c20226d656972796f207569222c20226b686d6572207569222c202274756e6761222c20226c616f207569222c20227261617669222c202269736b6f6f6c6120706f7461222c20226c61746861222c20226c65656c617761646565222c20226d6963726f736f6674207961686569207569222c20226d6963726f736f6674206a68656e67686569207569222c20226d616c67756e20676f74686963222c202265737472616e67656c6f20656465737361222c20226d6963726f736f66742068696d616c617961222c20226d6963726f696c736f6674206e657720746169206c7565222c20226d6963726f736f66742070686167737061222c20226d6963726f736f667420746169206c65222c20226d6963726f736f6674207969206261697469222c20226d6f6e676f6c69616e206261697469222c20226d7620626f6c69222c20226d79616e6d61722074657874222c202263616d62726961206d617468223b207d202e77726170706572207b206261636b67726f756e642d696d6167653a2075726c28646174613a696d6167652f6a70673b6261736536342c2f396a2f34616171736b7a6a7267616261716161617161626161642f327763656161756462616b6a63616b676371676762677967626775676267636763616b67626775676271636862777566627175696368776c6277676f637163686472756e6468657265786d7462777377676279736762617365786962627175666361636964776b6a6478696e64773073656869736568697365686973656869736568697365
root@pmg:~/clamav#3. You should edit customsig.ndb and prefix the content with the appropriate Name, Type and Offset in the following format:
Name:Type:Offset:malware hex output
Such as:
Trojan.Win32.Emold.A:1:*:4d5a80000100000004001000ffff000040010000000000004000000000000000000000000000000000000000
Name is the virus name. Type is one of the following:
0 = any file
1 = Portable Executable (ie Windows exe)
2 = OLE2 component (e.g. a VBA script)
3 = HTML (normalised)
4 = Mail file
5 = Graphics
6 = ELF
7 = ASCII text file (normalised)
Offset is either * or an offset in bytes from the beginning of the file to where the hex string occurs. This is best left as * unless you know your where in the file your hex string occurs. Read the Clamav documentation if this is the case. For the virus name, I get it from virustotal.


4. Let test scan the suspicious file with the customsign.ndb.
Code:
root@pmg:~/clamav# clamscan -d customsign.ndb DHL\ INVOICE_AWB#9514950815.html
/root/clamav/DHL INVOICE_AWB#9514950815.html: Phishing/HTML.Generic.S1605.UNOFFICIAL FOUND
----------- SCAN SUMMARY -----------
Known viruses: 1
Engine version: 0.103.6
Scanned directories: 0
Scanned files: 1
Infected files: 1
Data scanned: 0.12 MB
Data read: 0.27 MB (ratio 0.46:1)
Time: 0.009 sec (0 m 0 s)
Start Date: 2022:08:17 12:25:03
End Date: 2022:08:17 12:25:03
root@pmg:~/clamav#5. If successful, host the customsign.ndb file at your local web server or github public gist. Add the custom database to your /etc/pmg/templates/freshclam.cf.in.
Code:
DatabaseCustomURL https://gist.githubusercontent.com/hat3ph/17c72297c3b94cc350fdb0b2651fc352/raw/customsign.hdb6. Restart freshclam service with the new settings.
Code:
pmgconfig sync --restart 17. Double check freshclam have download the customsign.ndb to clamav's database directory.
Code:
Aug 17 11:47:10 pmg pmgconfig[43564]: configuration change detected for 'clamav-freshclam', restarting
Aug 17 11:47:10 pmg freshclam[845]: Update process terminated
Aug 17 11:47:10 pmg freshclam[845]: Update process terminated
Aug 17 11:47:10 pmg systemd[1]: clamav-freshclam.service: Succeeded.
Aug 17 11:47:10 pmg systemd[1]: clamav-freshclam.service: Consumed 6.567s CPU time.
Aug 17 11:47:10 pmg freshclam[43678]: freshclam daemon 0.103.6 (OS: linux-gnu, ARCH: x86_64, CPU: x86_64)
Aug 17 11:47:10 pmg freshclam[43678]: ClamAV update process started at Wed Aug 17 11:47:10 2022
Aug 17 11:47:10 pmg freshclam[43678]: ClamAV update process started at Wed Aug 17 11:47:10 2022
Aug 17 11:47:20 pmg freshclam[43678]: WARNING: Your ClamAV installation is OUTDATED!
Aug 17 11:47:20 pmg freshclam[43678]: WARNING: Local version: 0.103.6 Recommended version: 0.103.7
Aug 17 11:47:20 pmg freshclam[43678]: DON'T PANIC! Read https://docs.clamav.net/manual/Installing.html
Aug 17 11:47:20 pmg freshclam[43678]: Your ClamAV installation is OUTDATED!
Aug 17 11:47:20 pmg freshclam[43678]: Local version: 0.103.6 Recommended version: 0.103.7
Aug 17 11:47:20 pmg freshclam[43678]: DON'T PANIC! Read https://docs.clamav.net/manual/Installing.html
Aug 17 11:47:20 pmg freshclam[43678]: daily.cld database is up-to-date (version: 26629, sigs: 1996952, f-level: 90, builder: raynman)
Aug 17 11:47:20 pmg freshclam[43678]: main.cld database is up-to-date (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr)
Aug 17 11:47:20 pmg freshclam[43678]: bytecode.cvd database is up-to-date (version: 333, sigs: 92, f-level: 63, builder: awillia2)
Aug 17 11:47:20 pmg freshclam[43678]: daily.cld database is up-to-date (version: 26629, sigs: 1996952, f-level: 90, builder: raynman)
Aug 17 11:47:20 pmg freshclam[43678]: main.cld database is up-to-date (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr)
Aug 17 11:47:20 pmg freshclam[43678]: bytecode.cvd database is up-to-date (version: 333, sigs: 92, f-level: 63, builder: awillia2)
Aug 17 11:47:25 pmg freshclam[43678]: Testing database: '/var/lib/clamav//tmp.076b79f9b2/clamav-907bf53145b4a9092c5222366ee257a1.tmp-customsign.ndb' ...
Aug 17 11:47:25 pmg freshclam[43678]: Testing database: '/var/lib/clamav//tmp.076b79f9b2/clamav-907bf53145b4a9092c5222366ee257a1.tmp-customsign.ndb' ...
Aug 17 11:47:25 pmg freshclam[43678]: Database test passed.
Aug 17 11:47:25 pmg freshclam[43678]: customsign.ndb updated (version: custom database, sigs: 3)
Aug 17 11:47:25 pmg freshclam[43678]: Database test passed.
Aug 17 11:47:25 pmg freshclam[43678]: customsign.ndb updated (version: custom database, sigs: 3)
Aug 17 11:47:25 pmg freshclam[43678]: Clamd successfully notified about the update.
Aug 17 11:47:25 pmg freshclam[43678]: Clamd successfully notified about the update.
Aug 17 11:47:25 pmg freshclam[43678]: --------------------------------------
Code:
root@pmg:/var/lib/clamav# ls
customsign.ndb main.cld daily.cld freshclam.dat bytecode.cvd
root@pmg:/var/lib/clamav#8. Run a test mail with the suspicious file and clamav should block or recognize it with your custom virus name. Make sure you enable the default block virus rule.
Code:
Delivered-To: user1@mydomain.com
Return-Path: user1@gmail.com
Received-SPF: pass (gmail.com ... _spf.google.com: Sender is authorized to use 'user1@gmail.com' in 'mfrom' identity (mechanism 'include:_netblocks.google.com' matched)) receiver=pmg.mydomain.com; identity=mailfrom; envelope-from="user1@gmail.com"; helo=mail-oa1-f66.google.com; client-ip=209.85.160.66
Received: from mail-oa1-f66.google.com (mail-oa1-f66.google.com [209.85.160.66])
by pmg.mydomain.com (Proxmox) with ESMTP
for <user1@mydomain.com>; Wed, 17 Aug 2022 11:50:20 +0800 (+08)
Received: by mail-oa1-f66.google.com with SMTP id 586e51a60fabf-10e615a36b0so13915502fac.1
for <user1@mydomain.com>; Tue, 16 Aug 2022 20:50:20 -0700 (PDT)
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=gmail.com; s=20210112;
h=to:subject:message-id:date:from:mime-version:from:to:cc;
bh=ZI/7FewB3Qhh1cHMOGGy/F6aL3Tpka7f9FO1A5v6iR8=;
b=HgojhIiFBfuKQHjyDlSpbEiEQWvpfromxnagpI+3gL4Dznnmy5ewfdkQ1IPkjiXpsu
WwUGvFp+jaUKYsNAga3Ef7Iq+kp4AB0vzBW4QzqThaut0EJ9oUwXFPQA1SzIU7dR/697
zsoFq9ieAmAl8hoJE3kaxr8oyJmVvfrX2pZkMpyzs1EOMZcllyOrWThAKuEdV1Be2BTb
mkZUfqUIVfXOY7QZuweKxuXqyIDh8lPx/FXH1N5XL4Q5jlXaougVnSH+US+P7hfGGnOZ
TwN+1NLFIaLLsST0hthnwD2tRZFdsgVcZ+93yocOEmmWJX4EQiXqwCDd+nHGtmT7XFgI
jxAg==
X-Google-DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=1e100.net; s=20210112;
h=to:subject:message-id:date:from:mime-version:x-gm-message-state
:from:to:cc;
bh=ZI/7FewB3Qhh1cHMOGGy/F6aL3Tpka7f9FO1A5v6iR8=;
b=Zm/x6HFSzCwYdB6luXINnej2t9Ze+RFcUrWkwR+0osAGL/2miynJ19zdltU2lMSKcE
UJUA/F6NHunkV3yemaUSEQKLiEuKb3LZhUvOHwQb4ISZPwYTHj6pCY55VaR3F92xtC8x
1Ngf5FMnediCylOxHXbkeu6rtmdYN7qPne8OOE2Bx11WGXhNjh3kdsWHvEWs4UxpYCIo
K6fgfiNPigd7fbFTkf4gl+0vb3QiF7NuGEAOjpbZ0hDoTKIuGYYmD4NWobs5iPn7HD+f
TxanaGTg3wFItTNuJsy3R0QjA60n/XmurN5ZiQHrB+fYxdaGdhAeevMubcNZk6VeGb0r
EY0A==
X-Gm-Message-State: ACgBeo2bSWW2J3lCOufLBnmNZOUieBYezfvvuR1Dz9BXKa5XBHlnwMhq
XOa8uuOz8UYLYvAW6na93aWEcajq161YizG0D/YmfR3z
X-Google-Smtp-Source: AA6agR6LDTob2WNDXJyEv/cR5n5AAv4XeyvRtfN7VXuLOrWm87ReuELYiy2EC0ARdjTEuGWqKD9gkeD5sgz6vUlvI/c=
X-Received: by 2002:a05:6870:a2d0:b0:11c:3148:c44c with SMTP id
w16-20020a056870a2d000b0011c3148c44cmr825474oak.38.1660708208456; Tue, 16 Aug
2022 20:50:08 -0700 (PDT)
MIME-Version: 1.0
From: user1 <user1@gmail.com>
Date: Wed, 17 Aug 2022 11:49:40 +0800
Message-ID: <CAKETK8GQ+V6Ai9W+1A7HkX5myvbBSu30ojVmzTVJ6VW0uDZ6jQ@mail.gmail.com>
Subject: testing
To: "user1" <user1@mydomain.com>
Content-Type: multipart/mixed; boundary="000000000000d77cdb05e667c27a"
X-Proxmox-VInfo: Phishing/HTML.Generic.S1605.UNOFFICIAL (clamav)
X-SPAM-LEVEL: Spam detection results: 1
AWL -1.537 Adjusted score from AWL reputation of From: address
BAYES_00 -1.9 Bayes spam probability is 0 to 1%
DKIM_INVALID 0.1 DKIM or DK signature exists, but is not valid
DKIM_SIGNED 0.1 Message has a DKIM or DK signature, not necessarily valid
FREEMAIL_FROM 0.001 Sender email is commonly abused enduser mail provider
HTML_ATTACHED 1 Contains .htm or .html attachment
HTML_MESSAGE 0.001 HTML included in message
HTML_TAG_BALANCE_HEAD 0.817 HTML has unbalanced "head" tags
KAM_DMARC_STATUS 0.01 Test Rule for DKIM or SPF Failure with Strict Alignment
KAM_HTMLINVOICE 3 Invoice scam
RCVD_IN_DNSWL_NONE -0.0001 Sender listed at https://www.dnswl.org/, no trust
RCVD_IN_MSPIKE_H3 0.001 Good reputation (+3)
RCVD_IN_MSPIKE_WL 0.001 Mailspike good senders
SPF_HELO_NONE 0.001 SPF: HELO does not publish an SPF Record
SPF_PASS -0.001 SPF: sender matches SPF record
T_HTML_ATTACH 0.01 HTML attachment to bypass scanning?
T_SCC_BODY_TEXT_LINE -0.01 -
--000000000000d77cdb05e667c27a
Content-Type: multipart/alternative; boundary="000000000000d77cd905e667c278"
--000000000000d77cd905e667c278
Content-Type: text/plain; charset="UTF-8"
testing
--000000000000d77cd905e667c278
Content-Type: text/html; charset="UTF-8"
<div dir="ltr">testing<br></div>
--000000000000d77cd905e667c278--
--000000000000d77cdb05e667c27a
Content-Type: text/html; charset="US-ASCII"; name="DHL INVOICE_AWB#9514950815.html"
Content-Disposition: attachment; filename="DHL INVOICE_AWB#9514950815.html"
Content-Transfer-Encoding: base64
Content-ID: <f_l6x2rpxj0>
X-Attachment-Id: f_l6x2rpxj0
Last edited: