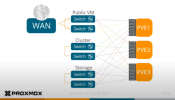
Dear,
I want to setup for ceph an full mesh network over dual 100gbe nic.
In the documentation "Deploy Hyper-Converged Ceph Cluster" it is recommended to split the public and cluster network of ceph.
If i am right, i have written that is recommended to have redundancy in the ceph network.
To my question.
If it is both recommended and i separate the "network" and "cluster" network and want to have additional the redundancy for ceph network.
I reach that with one dual(1x2) nic or i need two dual nics (2x2)?
If i need 2x2:
It is needed to have for public and cluster 100gbe each?
Or for one of both an 10gb would be enough?
I want to do an allNVMe Setup with mellanox 9300 MAX over 3 nodes.
Beginning 4 NVMe by node is planed.
Maximum is 8 NVMe by node
Many thanks for help
I want to setup for ceph an full mesh network over dual 100gbe nic.
In the documentation "Deploy Hyper-Converged Ceph Cluster" it is recommended to split the public and cluster network of ceph.
If i am right, i have written that is recommended to have redundancy in the ceph network.
To my question.
If it is both recommended and i separate the "network" and "cluster" network and want to have additional the redundancy for ceph network.
I reach that with one dual(1x2) nic or i need two dual nics (2x2)?
If i need 2x2:
It is needed to have for public and cluster 100gbe each?
Or for one of both an 10gb would be enough?
I want to do an allNVMe Setup with mellanox 9300 MAX over 3 nodes.
Beginning 4 NVMe by node is planed.
Maximum is 8 NVMe by node
Many thanks for help