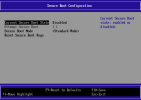
I'm trying to enable secure boot on a windows VM in preparation of the dreaded upgrade to Win11. However for some reason the option is greyed out in the VM bios (see screenshot). Not sure why or what needs to be changed. Config below if that helps.
Code:
agent: 1
args: -cpu 'host,+kvm_pv_unhalt,+kvm_pv_eoi,hv_vendor_id=NV43FIX,kvm=off'
balloon: 1024
bios: ovmf
boot: order=scsi0;ide2
cores: 16
cpu: host,hidden=1
cpuunits: 200
description: scsi1%3A VM-Storage%3Avm-102-disk-1,backup=0,iothread=1,size=1000G
efidisk0: VM-Storage:vm-108-disk-0,size=1M
hostpci0: 0000:05:00,pcie=1,x-vga=1
ide2: none,media=cdrom
machine: pc-q35-9.0
memory: 32768
name: BlueIris
net0: virtio=B2:A1:A6:E6:E7:A7,bridge=vmbr0,firewall=1,queues=16,tag=10
numa: 0
onboot: 1
ostype: win10
protection: 1
scsi0: VM-Storage:vm-108-disk-1,cache=writeback,discard=on,iothread=1,size=200G
scsi1: VM-Storage:vm-108-disk-4,backup=0,cache=writeback,discard=on,iothread=1,size=1000G
scsi2: VM-Storage:vm-108-disk-2,cache=writeback,discard=on,iothread=1,size=100G
scsihw: virtio-scsi-single
smbios1: uuid=43c0867d-1f21-43ee-a0eb-55db3f1a355d
sockets: 1
startup: order=1
tablet: 1
tags: windows
tpmstate0: VM-Storage:vm-108-disk-3,size=4M,version=v2.0
vmgenid: dfcf9182-a8a6-4396-8411-4f590ef3aae3

