I had opened another post because I had encountered a problem in the VM consoles that were constantly crashing. After a few seconds "connecting" appeared and we could still work for a minute or two; then yet another block and so on all VMs.
However, we then noticed that the shell also crashed for no reason, although for over a week we were able to work without any problems.
The only difference was creating two bridges using the GUI.
Commenting on the references to these Bridges in Interfaces, the shell resumes working, but obviously the VMs don't work anymore.
This is the contents of my configuration file; the Bridges configuration was created in the GUI using the default values:
The documentation states that when Proxmox is installed, vmbr0 is created, but we do not find any trace of it.
For your information:
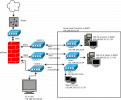
eno1 is the first card on the motherboard and is connected to the DMZ switch.
eno3 is another card on the motherboard and is connected to the LAN switch.
eno2 is currently not used, but I wanted to use it in bond with eno1
eno3 is not currently used, but I wanted to use it for an additional reserved area.
The other two NICs, on a PCIe card, I still don't know how to use.
This is the Server Configuration
However, we then noticed that the shell also crashed for no reason, although for over a week we were able to work without any problems.
The only difference was creating two bridges using the GUI.
Commenting on the references to these Bridges in Interfaces, the shell resumes working, but obviously the VMs don't work anymore.
This is the contents of my configuration file; the Bridges configuration was created in the GUI using the default values:
Code:
source /etc/network/interfaces.d/*
auto lo
iface lo inet loopback
auto eno1
iface eno1 inet dhcp
iface eno2 inet manual
iface eno3 inet manual
iface eno4 inet manual
iface ens1f0 inet manual
iface ens1f1 inet manual
#auto vmbr3
#iface vmbr3 inet static
# address 192.168.203.31/24
# gateway 192.168.203.1
# bridge-ports eno1
# bridge-stp off
# bridge-fd 0
#Bridge DMZ3
#auto vmbr1
#iface vmbr1 inet static
# address 192.168.201.31/24
# bridge-ports eno3
# bridge-stp off
# bridge-fd 0
#Bridge LAN1The documentation states that when Proxmox is installed, vmbr0 is created, but we do not find any trace of it.
For your information:
eno1 is the first card on the motherboard and is connected to the DMZ switch.
eno3 is another card on the motherboard and is connected to the LAN switch.
eno2 is currently not used, but I wanted to use it in bond with eno1
eno3 is not currently used, but I wanted to use it for an additional reserved area.
The other two NICs, on a PCIe card, I still don't know how to use.
This is the Server Configuration
- CPU(s) 24 x Intel(R) Xeon(R) CPU E5-2620 v2 @ 2.10GHz (2 Sockets)
- RAM 64GB
- Kernel Version Linux 5.11.22-5-pve #1 SMP PVE 5.11.22-10 (Tue, 28 Sep 2021 08:15:41 +0200)
- PVE Manager Version pve-manager/7.0-13/7aa7e488
Last edited: