Here is the overview of what I did in the end. The reason is the limitation from pmg as noted by Stoiko
https://forum.proxmox.com/threads/h...vd-bytecode-cvd-databases.117813/#post-510260
I had to spin up an additional proxmox mail gateway just to be able to do this for this customer.
The final requirements was to block password protected xls, xlsx and zip files. Additional requirement to not block password protected .pdf file.
If Arnaud Jacques did not help me by creating signatures for encrypted xls and xlsx files we would lost this customer.
So big shutout for his help and his company. We have been running his signatures and he has always been responsive and helpful if we needed help. He did not need to help me but he did it anyway.
https://www.securiteinfo.com/servic...e-of-zero-day-malwares-for-clamav.shtml?lg=en
I let the mail flow flow normally as before first via our primary proxmox mail gateway where I have all the rules, dns blocklists, eset scanning via icap, scanning via clamav ect. Then for this customer domains the mail flow is forwarded to the new proxmox mail gateway and then delivered to their mailboxes.
/etc/pmg/templates/clamd.conf.in
The main important settings: (to avoid false positives)
PhishingScanURLs false
AlertPhishingSSLMismatch false
To allow encrypted pdf:
ScanPDF false
/etc/pmg/templates/clamd.conf.in
Code:
#Automatically Generated by proxmox
LocalSocket /var/run/clamav/clamd.ctl
FixStaleSocket true
User clamav
ScanMail true
ScanArchive true
[% IF pmg.clamav.archiveblockencrypted %]
AlertEncrypted true
[% ELSE %]
AlertEncrypted false
[% END %]
MaxRecursion [% pmg.clamav.archivemaxrec %]
MaxFiles [% pmg.clamav.archivemaxfiles %]
MaxFileSize [% pmg.clamav.archivemaxsize %]
MaxScanSize [% pmg.clamav.maxscansize %]
MaxDirectoryRecursion 15
FollowDirectorySymlinks false
FollowFileSymlinks false
ReadTimeout 180
MaxThreads 12
MaxConnectionQueueLength 15
StreamMaxLength [% pmg.mail.maxsize %]
LogSyslog true
LogFacility LOG_LOCAL6
LogClean false
LogVerbose false
PidFile /var/run/clamav/clamd.pid
DatabaseDirectory /var/lib/clamav/
TemporaryDirectory /tmp
SelfCheck 3600
Foreground false
Debug false
ScanPE true
ScanOLE2 true
ScanHTML true
ScanPDF false
AlertBrokenExecutables true
ExitOnOOM false
LeaveTemporaryFiles false
AlgorithmicDetection true
ScanELF true
IdleTimeout 30
PhishingSignatures true
PhishingScanURLs false
AlertPhishingSSLMismatch false
AlertPhishingCloak false
DetectPUA false
ScanPartialMessages false
HeuristicScanPrecedence false
[% IF pmg.clamav.maxcccount %]
StructuredDataDetection true
StructuredMinCreditCardCount [% pmg.clamav.maxcccount %]
StructuredMinSSNCount [% pmg.clamav.maxcccount %]
[% ELSE %]
StructuredDataDetection false
[% END %]
CommandReadTimeout 5
SendBufTimeout 200
MaxQueue 100
LogFileMaxSize 0
Bytecode true
BytecodeSecurity TrustSigned
/etc/pmg/pmg.conf
Important here is:
archiveblockencrypted 1
clamav_heuristic_score 99
/etc/pmg/pmg.conf
Code:
section: admin
email proxmox@example.com
section: mail
banner ESMTP mx-sec.example.com
greylist 0
hide_received 0
maxsize 100000000
spf 0
tls 1
tlsheader 1
tlslog 1
verifyreceivers 550
section: spam
clamav_heuristic_score 99
maxspamsize 100000000
rbl_checks 0
use_awl 0
use_bayes 0
use_razor 0
section: clamav
archiveblockencrypted 1
archivemaxrec 20
section: spamquar
allowhrefs 0
viewimages 0
section: virusquar
allowhrefs 0
viewimages 0
In the /var/lib/clamav/ create office-pass.ndb
Code:
password-protected-xls-document:0:0:d0cf11e0*4d006900630072006f0073006f0066007400200045006e00680061006e006300650064002000430072007900700074006f0067007200610070006800690063002000500072006f0076006900640065007200200076
password-protected-xlsx-document:0:0:d0cf11e0*45006e0063007200790070007400650064005000610063006b0061006700650000
Thanks to Arnaud Jacques for creating this signatures his service
https://www.securiteinfo.com/servic...e-of-zero-day-malwares-for-clamav.shtml?lg=en
Make sure you set the rules properly I did it like this:
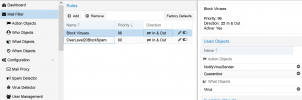
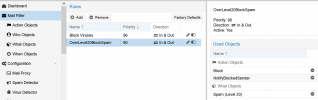
Bonus I wanted to make sure that every sender is properly notified that his messages was blocked because I don't want to recive calls about my message was not delivered and why.
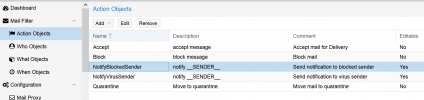
NotifyBlockedSender
Receiver: __SENDER__
Subject: Message delivery failure: __SUBJECT__
Body:
Your message to __RECEIVERS__ was blocked by the mail filtering system. If applicable resend your message following the solution below.
Summary:
Message subject: __SUBJECT__
Receiver mail address: __RECEIVERS__
Sender mail address: __SENDER__
Message ID: __MSGID__
Cause:
Reason for blocking message: Security policy by company ...
__SPAM_INFO__
Solution:
- Do not send messages that violate the security policy by ...
NotifyVirusSender
Receiver: __SENDER__
Subject: Message delivery failure: __SUBJECT__
Body:
Your message to __RECEIVERS__ was blocked by the mail filtering system. If applicable resend your message following the solution below.
Summary:
Message subject: __SUBJECT__
Receiver mail address: __RECEIVERS__
Sender mail address: __SENDER__
Message ID: __MSGID__
Cause:
Reason for blocking message: Security policy by ...
Detected __VIRUS_INFO__
Solution:
- Do not send messages that violate the security policy by ...
Make sure to add the correct SPF record for your mail gateway as well. Without that your notifications won't be working properly. Set a proper host-name for mail gateway and set SPF. Test notification to google check if message passed SPF.
Test by sending test password protected messages and see if the setup is blocking it correctly. When ready deploy to production.






