Hi,
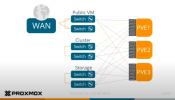
we have a proxmox / ceph cluster since 8 and 5 years up and runnng. Now specially some ceph servers are end of life and we want to replace them. We now want to change the network for best stability as we had some problems sometimes. Now we have 2 juniper Switches (all 10G LACP connected) with VLAN configured and 3 networks:
1: frontend vm and cluster network
2: storage network (ceph mons nfs etc..)
3: ceph osd network
recently a juniper switch crashed really baldy and all proxmox nodes as also ceph went down. Still we dont know why it hit so badly.
For this we want so separate physically more the networks.
Our plan is to use
1 OSD NETWORK: 2 x melanox 40gb active / passive - or is it possible stacked melanox with 40gb - or worth it?)
2 STORAGE NETWORK: 2 x Juniper 10G (for the mons and nds shares etc)
3 FRONTEND NETWORK : 2 X juniper 10G (only allow 1G for the vms set in proxmox) (a lot of vlans in this network)
having corosync configured for storage and frontend network as 2 rings.
Also he question ist it possible to have a second ceph ceph cluster (only mons) in the same network as the old ceph cluster?
what do you think? what considerations?
best regards
Philipp
we have a proxmox / ceph cluster since 8 and 5 years up and runnng. Now specially some ceph servers are end of life and we want to replace them. We now want to change the network for best stability as we had some problems sometimes. Now we have 2 juniper Switches (all 10G LACP connected) with VLAN configured and 3 networks:
1: frontend vm and cluster network
2: storage network (ceph mons nfs etc..)
3: ceph osd network
recently a juniper switch crashed really baldy and all proxmox nodes as also ceph went down. Still we dont know why it hit so badly.
For this we want so separate physically more the networks.
Our plan is to use
1 OSD NETWORK: 2 x melanox 40gb active / passive - or is it possible stacked melanox with 40gb - or worth it?)
2 STORAGE NETWORK: 2 x Juniper 10G (for the mons and nds shares etc)
3 FRONTEND NETWORK : 2 X juniper 10G (only allow 1G for the vms set in proxmox) (a lot of vlans in this network)
having corosync configured for storage and frontend network as 2 rings.
Also he question ist it possible to have a second ceph ceph cluster (only mons) in the same network as the old ceph cluster?
what do you think? what considerations?
best regards
Philipp