Same problem here. I have used a lot of my time to try and fine tune proxmox for our mailflow and still can't get detection rate to be better. You can also test your proxmox with
https://emailsecuritytester.com/ and see what score you will get. Yes you can say they tune this test for their solution but why would you not implement some things into proxmox as well. It should be better at detecting malicious messages.
Some of my old posts here should update my setup I have advance it quite a bit still not good enough
https://forum.proxmox.com/threads/s...mx-filter-in-reply-to-field.80037/post-354681
The worst thing is there is no deep detection of links or files. We even purchased securiteinfo.com it helps a bit but still not where it should be. I have a lot of high custom scores defined for spam assasin again it's a never ending story of changing the weights of the system it will never be good enough. If the scores are too high there will be a lot of false positives if the scores are too low there will be too much spam. It's hard to know the quality of spam assasin score that you can increase by a lot without getting a lot of false positives.
I have already increased some of the scores for some detection's from defaults but it's a never ending story of tuning the weights of the system...
Example two malicious messages from today:
connect from un.unrepeatedshow.com[194.41.47.92]
They are now on some blocklists but they have not been before when we got the message. Having more DNSBL is not a solution so many false positives if you do that...
I am only using b.barracudacentral.org;zen.spamhaus.org;bl.mailspike.net;dnsbl.sorbs.net;bl.spamcop.net and I won't be using any more I have found that a lot of DNSBL are really poor quality.
https://www.abuseipdb.com/check/194.41.47.92
https://mxtoolbox.com/SuperTool.aspx?action=blacklist%3a81.88.48.54
The link if you click on it it's different
https://mail.oldcoinbuy.com/g00h/index.php?
Yes it's Phishing
https://www.virustotal.com/gui/url/...1810518498bea97b7227e89d1dece693603?nocache=1
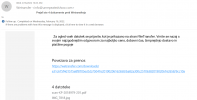
First one:
X-SPAM-LEVEL: Spam detection results: 3
DKIM_SIGNED 0.1 Message has a DKIM or DK signature, not necessarily valid
DKIM_VALID -0.5 Message has at least one valid DKIM or DK signature
DKIM_VALID_AU -0.1 Message has a valid DKIM or DK signature from author's domain
DKIM_VALID_EF -0.1 Message has a valid DKIM or DK signature from envelope-from domain
GOOG_MALWARE_DNLD 1 File download via Google - Malware?
HTML_MESSAGE 0.001 HTML included in message
HTTPS_HTTP_MISMATCH 3 -
KAM_GOOGLE_REDIR 0.5 Message contains a google URL redirector link
MIME_HTML_ONLY 0.1 Message only has text/html MIME parts
SPF_HELO_NONE 0.001 SPF: HELO does not publish an SPF Record
SPF_PASS -0.5 SPF: sender matches SPF record
T_SCC_BODY_TEXT_LINE -0.01 -
Second one:
connect from authsmtp04.register.it[81.88.48.54]
https://www.abuseipdb.com/check/81.88.48.54
https://mxtoolbox.com/SuperTool.aspx?action=blacklist:81.88.48.54&run=toolpage
They are not on any blocklist.
The link will download malicious file:
https://sibuceomexico.com.mx/rqcuatonuetseis/lua-oarse-outqatqttmommhuvi
https://www.virustotal.com/gui/file...17d9e434f1d2489f1cca38d74c80279734a?nocache=1
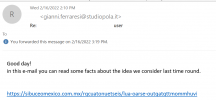
X-SPAM-LEVEL: Spam detection results: 0
HTML_MESSAGE 0.001 HTML included in message
KAM_DMARC_STATUS 0.01 Test Rule for DKIM or SPF Failure with Strict Alignment
RCVD_IN_DNSWL_LOW -0.7 Sender listed at
https://www.dnswl.org/, low trust
RCVD_IN_MSPIKE_H3 0.001 Good reputation (+3)
RCVD_IN_MSPIKE_WL 0.001 Mailspike good senders
SPF_HELO_PASS -0.001 SPF: HELO matches SPF record
SPF_PASS -0.5 SPF: sender matches SPF record
T_SCC_BODY_TEXT_LINE -0.01 -
How are you going to tune this? It's very hard or just impossible to detect this.
The servers are fresh not on any blocklist yet so good luck blocking this messages with proxmox.
Once the message is delivered it's too late the damage is already done. I don't have a way and don't want to scrub this malicious messages from all our mail systems it's not sustainable.