Hello,
I have followed the instructions HERE to install Proxmox packages on top of a fully updated and upgraded Debian 11 stable image.
I am able to log in to the node via the web interface, join it to my cluster, and adopt it into my Ceph cluster.
I am running into an issue where I can not start or migrate an LXC into this node. I get similar errors to those described HERE but I am seeing this despite the pve-lxc >= 5.0.2-2 "fix" being present.
This may be related to an error message I am seeing onscreen on boot.
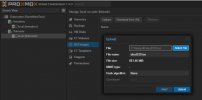
I am also having trouble uploading uploading filed to local storage similar to those described HERE. I am observing that no mater the path on my local system the webUI is always loading C:\fakepath\. I have tried this with multiple web browsers and my other cluster node is not having the same problem.
Thanks for any help you can provide.
I have followed the instructions HERE to install Proxmox packages on top of a fully updated and upgraded Debian 11 stable image.
I am able to log in to the node via the web interface, join it to my cluster, and adopt it into my Ceph cluster.
I am running into an issue where I can not start or migrate an LXC into this node. I get similar errors to those described HERE but I am seeing this despite the pve-lxc >= 5.0.2-2 "fix" being present.
This may be related to an error message I am seeing onscreen on boot.

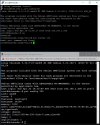
Code:
root@thinnode:/etc/pve/lxc# ls
100.conf
root@thinnode:/etc/pve/lxc# pct config 100
bash: pct: command not found
root@thinnode:/etc/pve/lxc# cat 100.conf
arch: amd64
cores: 4
features: nesting=1
hostname: ThinTest
memory: 4012
net0: name=eth0,bridge=vmbr0,hwaddr=BE:32:2F:AF:6B:05,ip=dhcp,type=veth
ostype: ubuntu
rootfs: local:100/vm-100-disk-0.raw,size=8G
swap: 0
unprivileged: 1
root@thinnode:/etc/pve/lxc# pveversion -v
proxmox-ve: 7.4-1 (running kernel: 5.10.0-21-amd64)
pve-manager: 7.4-3 (running version: 7.4-3/9002ab8a)
pve-kernel-5.15: 7.4-1
pve-kernel-5.15.104-1-pve: 5.15.104-2
ceph: 17.2.5-pve1
ceph-fuse: 17.2.5-pve1
corosync: 3.1.7-pve1
criu: 3.15-1+pve-1
glusterfs-client: 9.2-1
ifupdown: residual config
ifupdown2: 3.1.0-1+pmx3
libjs-extjs: 7.0.0-1
libknet1: 1.24-pve2
libproxmox-acme-perl: 1.4.4
libproxmox-backup-qemu0: 1.3.1-1
libproxmox-rs-perl: 0.2.1
libpve-access-control: 7.4-2
libpve-apiclient-perl: 3.2-1
libpve-common-perl: 7.3-4
libpve-guest-common-perl: 4.2-4
libpve-http-server-perl: 4.2-3
libpve-rs-perl: 0.7.5
libpve-storage-perl: 7.4-2
libspice-server1: 0.14.3-2.1
lvm2: 2.03.11-2.1
lxc-pve: 5.0.2-2
lxcfs: 5.0.3-pve1
novnc-pve: 1.4.0-1
proxmox-backup-client: 2.4.1-1
proxmox-backup-file-restore: 2.4.1-1
proxmox-kernel-helper: 7.4-1
proxmox-mail-forward: 0.1.1-1
proxmox-mini-journalreader: 1.3-1
proxmox-offline-mirror-helper: 0.5.1-1
proxmox-widget-toolkit: 3.6.5
pve-cluster: 7.3-3
pve-container: 4.4-3
pve-docs: 7.4-2
pve-edk2-firmware: 3.20230228-2
pve-firewall: 4.3-1
pve-firmware: 3.6-4
pve-ha-manager: 3.6.0
pve-i18n: 2.12-1
pve-qemu-kvm: 7.2.0-8
pve-xtermjs: 4.16.0-1
qemu-server: 7.4-3
smartmontools: 7.2-pve3
spiceterm: 3.2-2
swtpm: 0.8.0~bpo11+3
vncterm: 1.7-1
zfsutils-linux: 2.1.9-pve1
root@thinnode:/etc/pve/lxc#
root@thinnode:/etc/pve/lxc# cat /tmp/lxc-100.log
lxc-start 100 20230425032310.992 INFO confile - ../src/lxc/confile.c:set_config_idmaps:2273 - Read uid map: type u nsid 0 hostid 100000 range 65536
lxc-start 100 20230425032310.992 INFO confile - ../src/lxc/confile.c:set_config_idmaps:2273 - Read uid map: type g nsid 0 hostid 100000 range 65536
lxc-start 100 20230425032310.993 INFO lxccontainer - ../src/lxc/lxccontainer.c:do_lxcapi_start:998 - Set process title to [lxc monitor] /var/lib/lxc 100
lxc-start 100 20230425032310.993 DEBUG lxccontainer - ../src/lxc/lxccontainer.c:wait_on_daemonized_start:859 - First child 3673 exited
lxc-start 100 20230425032310.994 INFO lsm - ../src/lxc/lsm/lsm.c:lsm_init_static:38 - Initialized LSM security driver AppArmor
lxc-start 100 20230425032310.994 INFO conf - ../src/lxc/conf.c:run_script_argv:338 - Executing script "/usr/share/lxc/hooks/lxc-pve-prestart-hook" for container "100", config section "lxc"
lxc-start 100 20230425032311.623 INFO cgfsng - ../src/lxc/cgroups/cgfsng.c:unpriv_systemd_create_scope:1227 - Running privileged, not using a systemd unit
lxc-start 100 20230425032311.623 DEBUG seccomp - ../src/lxc/seccomp.c:parse_config_v2:656 - Host native arch is [3221225534]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "reject_force_umount # comment this to allow umount -f; not recommended"
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:524 - Set seccomp rule to reject force umounts
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:524 - Set seccomp rule to reject force umounts
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:524 - Set seccomp rule to reject force umounts
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "[all]"
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "kexec_load errno 1"
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding native rule for syscall[246:kexec_load] action[327681:errno] arch[0]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[246:kexec_load] action[327681:errno] arch[1073741827]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[246:kexec_load] action[327681:errno] arch[1073741886]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "open_by_handle_at errno 1"
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding native rule for syscall[304:open_by_handle_at] action[327681:errno] arch[0]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[304:open_by_handle_at] action[327681:errno] arch[1073741827]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[304:open_by_handle_at] action[327681:errno] arch[1073741886]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "init_module errno 1"
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding native rule for syscall[175:init_module] action[327681:errno] arch[0]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[175:init_module] action[327681:errno] arch[1073741827]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[175:init_module] action[327681:errno] arch[1073741886]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "finit_module errno 1"
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding native rule for syscall[313:finit_module] action[327681:errno] arch[0]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[313:finit_module] action[327681:errno] arch[1073741827]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[313:finit_module] action[327681:errno] arch[1073741886]
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "delete_module errno 1"
lxc-start 100 20230425032311.623 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding native rule for syscall[176:delete_module] action[327681:errno] arch[0]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[176:delete_module] action[327681:errno] arch[1073741827]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[176:delete_module] action[327681:errno] arch[1073741886]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "ioctl errno 1 [1,0x9400,SCMP_CMP_MASKED_EQ,0xff00]"
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:547 - arg_cmp[0]: SCMP_CMP(1, 7, 65280, 37888)
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding native rule for syscall[16:ioctl] action[327681:errno] arch[0]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:547 - arg_cmp[0]: SCMP_CMP(1, 7, 65280, 37888)
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[16:ioctl] action[327681:errno] arch[1073741827]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:547 - arg_cmp[0]: SCMP_CMP(1, 7, 65280, 37888)
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[16:ioctl] action[327681:errno] arch[1073741886]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:807 - Processing "keyctl errno 38"
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding native rule for syscall[250:keyctl] action[327718:errno] arch[0]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[250:keyctl] action[327718:errno] arch[1073741827]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:do_resolve_add_rule:564 - Adding compat rule for syscall[250:keyctl] action[327718:errno] arch[1073741886]
lxc-start 100 20230425032311.624 INFO seccomp - ../src/lxc/seccomp.c:parse_config_v2:1017 - Merging compat seccomp contexts into main context
lxc-start 100 20230425032311.917 ERROR apparmor - ../src/lxc/lsm/apparmor.c:run_apparmor_parser:916 - Failed to run apparmor_parser on "/var/lib/lxc/100/apparmor/lxc-100_<-var-lib-lxc>": apparmor_parser: Unable to replace "lxc-100_</var/lib/lxc>". Profile doesn't conform to protocol
lxc-start 100 20230425032311.917 ERROR apparmor - ../src/lxc/lsm/apparmor.c:apparmor_prepare:1088 - Failed to load generated AppArmor profile
lxc-start 100 20230425032311.917 ERROR start - ../src/lxc/start.c:lxc_init:876 - Failed to initialize LSM
lxc-start 100 20230425032311.917 ERROR start - ../src/lxc/start.c:__lxc_start:2027 - Failed to initialize container "100"
lxc-start 100 20230425032311.917 WARN cgfsng - ../src/lxc/cgroups/cgfsng.c:cgfsng_payload_destroy:555 - Uninitialized limit cgroup
lxc-start 100 20230425032311.917 WARN cgfsng - ../src/lxc/cgroups/cgfsng.c:cgfsng_monitor_destroy:881 - Uninitialized monitor cgroup
lxc-start 100 20230425032311.917 INFO conf - ../src/lxc/conf.c:run_script_argv:338 - Executing script "/usr/share/lxc/hooks/lxc-pve-poststop-hook" for container "100", config section "lxc"
lxc-start 100 20230425032312.484 INFO conf - ../src/lxc/conf.c:run_script_argv:338 - Executing script "/usr/share/lxcfs/lxc.reboot.hook" for container "100", config section "lxc"
lxc-start 100 20230425032312.988 ERROR lxccontainer - ../src/lxc/lxccontainer.c:wait_on_daemonized_start:870 - No such file or directory - Failed to receive the container state
lxc-start 100 20230425032312.988 ERROR lxc_start - ../src/lxc/tools/lxc_start.c:main:306 - The container failed to start
lxc-start 100 20230425032312.988 ERROR lxc_start - ../src/lxc/tools/lxc_start.c:main:309 - To get more details, run the container in foreground mode
lxc-start 100 20230425032312.988 ERROR lxc_start - ../src/lxc/tools/lxc_start.c:main:311 - Additional information can be obtained by setting the --logfile and --logpriority optionsI am also having trouble uploading uploading filed to local storage similar to those described HERE. I am observing that no mater the path on my local system the webUI is always loading C:\fakepath\. I have tried this with multiple web browsers and my other cluster node is not having the same problem.

Thanks for any help you can provide.
Last edited: