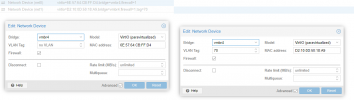
I have an Ubuntu VM for which I want two interfaces: one interface for untagged traffic (i.e. VLAN 1) and one for a specific VLAN. I am not quite sure about the correct way to configure this in Proxmox.
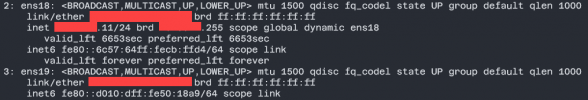
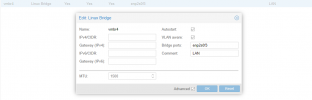
I have a VLAN aware bridge where a VLANs are trunked (vmbr4) and if I create a VM with a network card either untagged or tagged (e.g. with VLAN 200), that interface on the Ubuntu VM is assigned an IP address in the correct VLAN range.
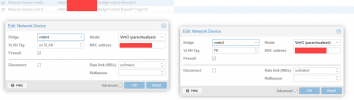
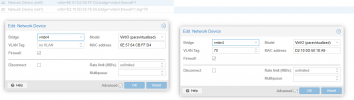
However, if I add a second network card, that interface shows up (ens19 in the below snapshot), but the link is DOWN and is not assigned an IP from the DHCP.
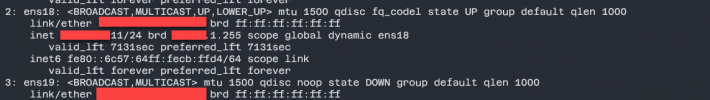
Am I missing something or is this the wrong approach to assigning multiple network interfaces / vlans to a VM?
I have a VLAN aware bridge where a VLANs are trunked (vmbr4) and if I create a VM with a network card either untagged or tagged (e.g. with VLAN 200), that interface on the Ubuntu VM is assigned an IP address in the correct VLAN range.
However, if I add a second network card, that interface shows up (ens19 in the below snapshot), but the link is DOWN and is not assigned an IP from the DHCP.

Am I missing something or is this the wrong approach to assigning multiple network interfaces / vlans to a VM?