I upgraded two of my home servers to Debian Trixie + Proxmox 9.0 Beta. I have the following issues and questions:
1) vGPU unlock patching does not work. The patch program gives the following errors when attempting to patch the nvidia drivers: "/usr/bin/patch: ** patch line 9 contains NUL byte." I have worked around this issue by patching the drivers with a Debian 12 distribution.
2) How would I go about adding the AMD (Ryzen) microcode updates and Intel microcode updates to these two systems? Is it a separate repo I have to add / configure with APT?
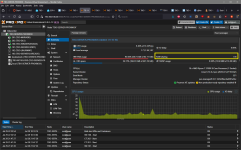
3) On my main server rig, I have two VMs that run all the time, Win Server 2025 and Win11, both updated to the same base kernel / build. On Proxmox 8.x, KSM sharing would kick in after about 5 minutes of them starting and share about 7 GB of RAM. With Proxmox 9 on Trixie, KSM sharing never kicks in. Is there a reason for this or is this broken / bugged?
Thanks.
1) vGPU unlock patching does not work. The patch program gives the following errors when attempting to patch the nvidia drivers: "/usr/bin/patch: ** patch line 9 contains NUL byte." I have worked around this issue by patching the drivers with a Debian 12 distribution.
2) How would I go about adding the AMD (Ryzen) microcode updates and Intel microcode updates to these two systems? Is it a separate repo I have to add / configure with APT?
3) On my main server rig, I have two VMs that run all the time, Win Server 2025 and Win11, both updated to the same base kernel / build. On Proxmox 8.x, KSM sharing would kick in after about 5 minutes of them starting and share about 7 GB of RAM. With Proxmox 9 on Trixie, KSM sharing never kicks in. Is there a reason for this or is this broken / bugged?

Thanks.






