Hi,
Fairly new to Proxmox, coming from about 20 years of Vmware. This seems to be a common secenerio with Proxmox. But it've been racking my brain for about a week now. Scowering the Forums to try to resolve it.
I am limited to 1 physical NIC, in which I was planning on doing an Ethernet Passthrough. How it should be. I have access to other virtual IP's from the provider, but I think it's all going to lead back to a Double NAT scenerio
I have a basic IP masquarade on the Bridges as the ISP doesn't like multiple Mac Addresses Broadcasting. Neither do I actually.
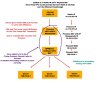
Proxmox is running fine, with Internet WAN. Management Port. OPNSense is configured and routing basic traffic to VM's inside of it to the LAN virtual Bridge. Example, I can surf the web our ping from VM's from inside the OPNsense LAN ip gateway behind the OPNSense Firewall
But where I am stuck is, I can't Port Forwards anything from the outside on Public IP's and get it to OPNsense for port Forwards.
Example, Web Server on port 80,443, or Mailsever 587, 25, 143, you name it
Packets seem to stop before OPNsense. So there is no OPNsense Port Forwards
This appears to be a common scenerio Since tons of people are using Proxmox, and running firewalls inside of it.
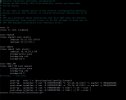
Tried Multiple Varients of Network configs but Manual Bridge Routing isn't my thing.
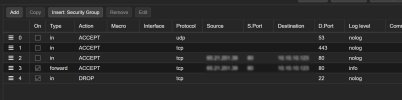
Also, trying the Proxmox Firewall Forwarding which doesn't seem to work for me
Any Help would be appreciated
Fairly new to Proxmox, coming from about 20 years of Vmware. This seems to be a common secenerio with Proxmox. But it've been racking my brain for about a week now. Scowering the Forums to try to resolve it.
I am limited to 1 physical NIC, in which I was planning on doing an Ethernet Passthrough. How it should be. I have access to other virtual IP's from the provider, but I think it's all going to lead back to a Double NAT scenerio
I have a basic IP masquarade on the Bridges as the ISP doesn't like multiple Mac Addresses Broadcasting. Neither do I actually.
Proxmox is running fine, with Internet WAN. Management Port. OPNSense is configured and routing basic traffic to VM's inside of it to the LAN virtual Bridge. Example, I can surf the web our ping from VM's from inside the OPNsense LAN ip gateway behind the OPNSense Firewall
But where I am stuck is, I can't Port Forwards anything from the outside on Public IP's and get it to OPNsense for port Forwards.
Example, Web Server on port 80,443, or Mailsever 587, 25, 143, you name it
Packets seem to stop before OPNsense. So there is no OPNsense Port Forwards
This appears to be a common scenerio Since tons of people are using Proxmox, and running firewalls inside of it.
Tried Multiple Varients of Network configs but Manual Bridge Routing isn't my thing.
Also, trying the Proxmox Firewall Forwarding which doesn't seem to work for me
Any Help would be appreciated
Attachments
Last edited: