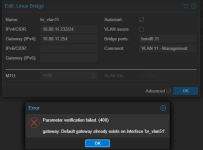
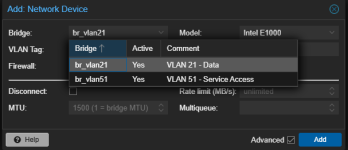
When creating a new VM or adding a network device to a VM, a dialog like this is shown, where the user chooses which network bridge to attach:
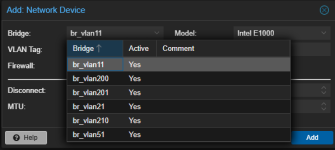
A similar dialog is also shown when choosing network(s) for Corosync to create or join a cluster.
My questions:
1. Is there a way to limit or filter out the bridges presented? In the example shown, I would like to prevent my users from being able to choose the bridges on the system which are not for VMs to use, as they are being used for SAN or management traffic.
2. Barring that, it would be useful for the "Comment" field to be able to warn people away from choosing a bridge. Is there a way to populate the comment field?
-Cheers,
speck

A similar dialog is also shown when choosing network(s) for Corosync to create or join a cluster.
My questions:
1. Is there a way to limit or filter out the bridges presented? In the example shown, I would like to prevent my users from being able to choose the bridges on the system which are not for VMs to use, as they are being used for SAN or management traffic.
2. Barring that, it would be useful for the "Comment" field to be able to warn people away from choosing a bridge. Is there a way to populate the comment field?
-Cheers,
speck