Hi all
I'm trying to create a cibersecurity lab.
I have added Kali, Ubuntu, Metasploit VMs in a 10.0.0.0/24 network in Poxmox
I have tried to capture pakets using Wireshark from Kali, but it only see its own packets.
I how you can help me, this is my current configuration:
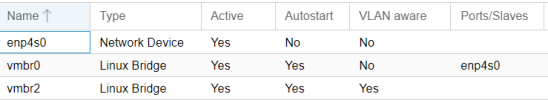
NODE Netkwork:
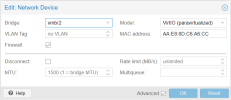
KALI (and other) machine(s):
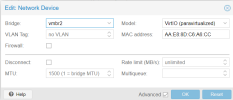
Every VM has a fixed IP address 10.0.0.0/24, the gateway is 10.0.0.1
This is the interface config in Kali
cat /etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
#Carlos, hacer promiscuo persistente
auto eth0
iface eth0 inet static
address 10.0.0.9
netmask 255.255.255.0
gateway 10.0.0.1
dns-nameservers 9.9.9.9,8.8.8.8
iface eth0 inet manual
up ifconfig eth0 promisc
down ifconfig eth0 down
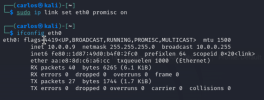
This is de "ip a" command result in Kali:
Firewalls are off in each VM and in the host
Al the VM have static IPs and there is a Ububtu Server with 2 NICS doing the router job using IPTables. It has two addresses 10.0.0.1 and 192.168.1.xx.
I'd like to be able to make Kali sniff the 10.0.0.0/24 network, I don't want to expose my home network.
I'll thank any help
Thank you so much!
I'm trying to create a cibersecurity lab.
I have added Kali, Ubuntu, Metasploit VMs in a 10.0.0.0/24 network in Poxmox
I have tried to capture pakets using Wireshark from Kali, but it only see its own packets.
I how you can help me, this is my current configuration:
NODE Netkwork:

KALI (and other) machine(s):

Every VM has a fixed IP address 10.0.0.0/24, the gateway is 10.0.0.1
This is the interface config in Kali
cat /etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
#Carlos, hacer promiscuo persistente
auto eth0
iface eth0 inet static
address 10.0.0.9
netmask 255.255.255.0
gateway 10.0.0.1
dns-nameservers 9.9.9.9,8.8.8.8
iface eth0 inet manual
up ifconfig eth0 promisc
down ifconfig eth0 down
This is de "ip a" command result in Kali:
└─$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether aa:e8:8d:c6:a6:cc brd ff:ff:ff:ff:ff:ff
inet 10.0.0.9/24 brd 10.0.0.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::a8e8:8dff:fec6:a6cc/64 scope link proto kernel_ll
valid_lft forever preferred_lft forever
Firewalls are off in each VM and in the host
Al the VM have static IPs and there is a Ububtu Server with 2 NICS doing the router job using IPTables. It has two addresses 10.0.0.1 and 192.168.1.xx.
I'd like to be able to make Kali sniff the 10.0.0.0/24 network, I don't want to expose my home network.
I'll thank any help
Thank you so much!
Attachments
Last edited: