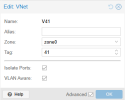
Good morning,
I want to have a cluster-wide vnet, which uses port isolation so no VM in it is able to communicate with another VM in the same vnet.
However this only works between 2 or more VMs running on the same host and vnet.
VMs in this vnet running on different hosts can perfectly communicate with eachother.
Can anybody point me in the right direction on how to achieve this:
- to have a vnet whose members are isolated from eachother, no matter on which hosts they run.
Thanks
Vaddi
I want to have a cluster-wide vnet, which uses port isolation so no VM in it is able to communicate with another VM in the same vnet.
However this only works between 2 or more VMs running on the same host and vnet.
VMs in this vnet running on different hosts can perfectly communicate with eachother.
Can anybody point me in the right direction on how to achieve this:
- to have a vnet whose members are isolated from eachother, no matter on which hosts they run.
Thanks
Vaddi