In light of Broadcom's idiotic behaviour I have decided to switch from VMware.
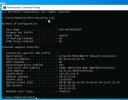
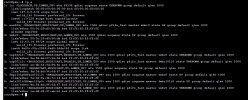
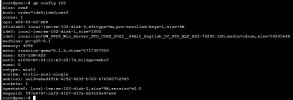
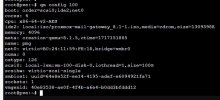
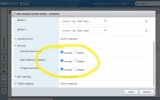
I'm attempting to evaluate Proxmox products but don't have any spare bare metal right now so I've installed PVE/PBS/PMG as vm's inside of a VMware environment where I had plenty of spare cpu/ram/disk to dedicate to this test. Everything installed and seemed to work fine, vm's were all accessible but in hindsight if I move ahead with Proxmox as a bare metal hypervisor solution the PBS/PMG vm's on VMware don't make sense so I re-created them as vm's in the PVE. Everything seemed to be fine and the vm's re-installed no problem. When I tried to access the vm's with a PC on the main LAN I could not access the PMG/PBS vm's like I could before even though they have IPs on the same LAN subnet as the PC I'm using and PVE vm. Thought this may be a wierd quirkyness with the PVE server using VMXNET3 adapter so I recreated all of this environment using Intel E1000 virtual adapter on the PVE server vm with same results. I don't know the PBS or PMG products or Linux in general as well as a Windows so I created a Winders server vm inside the PVE environment. After going thru the setup the Windows install sets the nic as dhcp as default. I logged in to Windows thru the PVE vm console and tried to access the PBS and PMG vm's and that worked fine. The Windows server didn't have internet access and it could not access any network device outside of the PVE environment. When I checked the ipconfig at command line it did receive valid dhcp information from my dhcp server which is outside of the PVE vm. Its ip address made sense for next available and gateway / DNS servers were also accurate. So... somehow the PVE server allowed the Windows vm to pull a dhcp address but not all it to fully communicate with that network after that? This makes no sense to me now. I found the PVE firewall setting and also the firewall setting for each of the vm's inside PVE and verified they were all off. The Windows vm firewall has all been turned off.
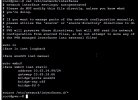
It's like the PVE server is not allowing the vm's to communicate past PVE itself? I did as much googling as I could and I found articles about setting the /proc/sys/net/ipv4/ip_forward file and setting it to 1. I Rebooted everything, no luck.
I also added this line to the interfaces file
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
Rebooted everything again, still no luck.
I'm stumped so far. Probably something small I'm missing but at the same time, such a basic setup and test, I'd assume out of the box a PVE vm should be able to access the internet or other resources past the PVE server?
Thanks in advance.
I'm attempting to evaluate Proxmox products but don't have any spare bare metal right now so I've installed PVE/PBS/PMG as vm's inside of a VMware environment where I had plenty of spare cpu/ram/disk to dedicate to this test. Everything installed and seemed to work fine, vm's were all accessible but in hindsight if I move ahead with Proxmox as a bare metal hypervisor solution the PBS/PMG vm's on VMware don't make sense so I re-created them as vm's in the PVE. Everything seemed to be fine and the vm's re-installed no problem. When I tried to access the vm's with a PC on the main LAN I could not access the PMG/PBS vm's like I could before even though they have IPs on the same LAN subnet as the PC I'm using and PVE vm. Thought this may be a wierd quirkyness with the PVE server using VMXNET3 adapter so I recreated all of this environment using Intel E1000 virtual adapter on the PVE server vm with same results. I don't know the PBS or PMG products or Linux in general as well as a Windows so I created a Winders server vm inside the PVE environment. After going thru the setup the Windows install sets the nic as dhcp as default. I logged in to Windows thru the PVE vm console and tried to access the PBS and PMG vm's and that worked fine. The Windows server didn't have internet access and it could not access any network device outside of the PVE environment. When I checked the ipconfig at command line it did receive valid dhcp information from my dhcp server which is outside of the PVE vm. Its ip address made sense for next available and gateway / DNS servers were also accurate. So... somehow the PVE server allowed the Windows vm to pull a dhcp address but not all it to fully communicate with that network after that? This makes no sense to me now. I found the PVE firewall setting and also the firewall setting for each of the vm's inside PVE and verified they were all off. The Windows vm firewall has all been turned off.
It's like the PVE server is not allowing the vm's to communicate past PVE itself? I did as much googling as I could and I found articles about setting the /proc/sys/net/ipv4/ip_forward file and setting it to 1. I Rebooted everything, no luck.
I also added this line to the interfaces file
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
Rebooted everything again, still no luck.
I'm stumped so far. Probably something small I'm missing but at the same time, such a basic setup and test, I'd assume out of the box a PVE vm should be able to access the internet or other resources past the PVE server?
Thanks in advance.
Last edited: