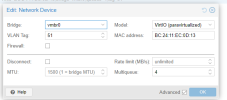
Are you hooking the machine to a managed switch, AND is the port or ports you are using set up to be trunk ports (i.e., tagged ports)? Also, what do the firewall rules for you VLAN look like? The only time I personally have experienced this is when I set up my Proxmox machine to be VLAN aware and connected it to access/un-tagged port, or visa versa, when I set up a new install of Proxmox, and haven't yet modified my vmbr to be LAN aware, and I connected it to a trunked port. Both situations will break your network connection to the box.
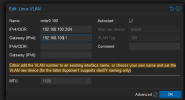
Now I assumed VLAN 40 was you management VLAN? If not that could be the problem. In the example I shared with you, VLAN 100 is my management VLAN, and the IP address that I set vmbr0.100 to is my management interface for Proxmox. I do not need to do anything to configure other VLANs other than the following:
1. Make sure the VLANs exist in my firewall router. If you are using a layer 3 switch, I would imagine you have to create them there as well. But I have no experience with L3 switches. I do everything in my firewall/router machine (pfSense)
2. VLANs only work on managed switches. If you are trying to connect through an unmanaged switch, that will be a problem
3. Your managed switch needs to proved a trunk (tagged) port to the NIC you are using for your management interface/vmbr0
4. Your chain of network devices all the way back to your WAN has to be connected via trunked ports. So my managed switch is connected to my pfSense box via trunk ports.
5. Set your firewall (or routing rules/ACLs in an L3 switch) to allow inter VLAN communication as you see fit. Whatever VLAN your PC is on has to be able to traverse to your management VLAN or you won't be able to access the gui/log in via SSH
Where does the management network reside when I've got multiple VLANs?
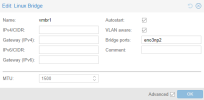
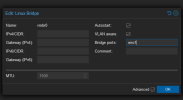
It only resides in the network hardware configuration for individual VMs and CTs (one of the earlier pictures I attached). As long as your vmbr0 (not vmbr0.40) is VLAN aware, it will pass the traffic to your network, assuming all the conditions I outlined above. vmbr0.40 is only applicable to your management interface/SSH into the Proxmox host.
At the risk of being overly verbose here, let me explain my set up a little more and hopefully it will illustrate the point for you. My network consists of a cable modem for a WAN which feeds into my pfSense box (firewall/router). I run a link from my pfSense box to my managed switch (on a trunk port). My LAN is segmented into 6 VLANs: Trusted, Untrusted, TVs, IOT, Guest, and Management. Of the 24 ports on my switch, some are trunked (I have to set this up in the switch console) and connect to my Proxmox machines as well as to my WAP, which is VLAN aware and had up to 8 SSIDs. The remaining ports are access ports (dedicated to only one VLAN). Some of those are dedicated to the Trusted VLAN, some to the Untrusted VLAN, some to the IOT VLAN. None are dedicated to Guests, TVs or Management, just because I don't need wired connections for those.
Inside my Proxmox boxes, you have seen how I configure my vmbr0 and vmbro.100. The IP address is the address of the server itself (GUI/SSH). The gateway points back to my router, always at 192.168.100.1. I don't need to provide any other gateways or routes, since it is all on one physical device. Proxmox does not require you to set up a gateway for each VLAN, as long as the gateway goes to your router.
When I set up a new VM or CT, I select which VLAN I want to be on at setup time. Or I can actually change it later if I want (like if using a template to spin up a new VM).
My home PC that I use to run/manage everything from sits on the Trusted VLAN. That VLAN, in firewall rules, can access everything in every other VLAN. My Guest, IOT, TV, Untrusted, and Management VLANs can only see the internet/WAN. They are not allowed to access the pfSense management interface, and they are not allowed to see into any other VLANs.
Each VLAN is on its own subnet and has its own DHCP server. I set up new VMs with DHCP and I control all the IP addressing through DHCP reservations in pfSense based on the mac address of the NIC in question.
When I need to log into a pfSense box or SSH into a VM, I do it from my home PC on the trusted VLAN. Even though that PC is on a completely different subnet/ip address range, the firewall rules let me access whatever I want on any VLAN