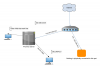
Hey guys,
Im trying to implement a VM with SecureLink which should be residing in the DMZ zone. The proxmox server has both nic bonded and connected to our main network 192.168.10.x which is connected to port 4 of our firewall/gateway. On port 5 i have the DMZ/network 192.168.42.1, nothing is physically connected port 5. The interface is pingable from the proxmox server and from everywhere, as the DMZ is not enforced yet. But when i setup statick IP on the VM 192.168.42.5 with gateway .1 i cant access anything. What am I missing here?
Thanks,
Mladen
Im trying to implement a VM with SecureLink which should be residing in the DMZ zone. The proxmox server has both nic bonded and connected to our main network 192.168.10.x which is connected to port 4 of our firewall/gateway. On port 5 i have the DMZ/network 192.168.42.1, nothing is physically connected port 5. The interface is pingable from the proxmox server and from everywhere, as the DMZ is not enforced yet. But when i setup statick IP on the VM 192.168.42.5 with gateway .1 i cant access anything. What am I missing here?
Thanks,
Mladen