Hello everyone! How are you?
First of all, I would like to thank you for your attention and apologize if there are any mistakes in English, since this is not my native language.
I am new to virtualized environments and have had a homelab at home for a few weeks.
I have about 4 virtual machines, running beautifully on my Proxmox host.
I have currently virtualized pfSense within my host and since then I have been using it as a router/firewall in my home, which has worked very well so far!
About 10 days ago, I decided to segment my guest and IoT network, since I have a Unifi and it is compatible with VLANs.
The problem with this is that according to the configuration I made, my 2 VLANs end up "leaking" tagged traffic to my untagged network.
Below, I will detail how my interfaces are configured.
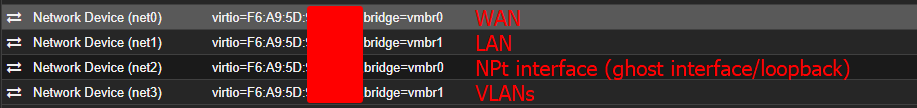
Here, we have the interfaces as they are configured in my pfSense: WAN, LAN, NPt (this interface being ghost, being used only to obtain an IPv6 prefix from my ISP) and my VLAN interface:
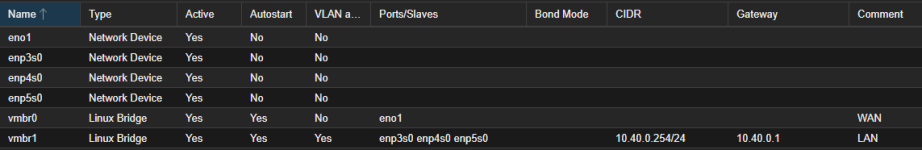
Here, we have how my proxmox is configured.
I have the vmbr0 bridge that has the eno1 interface, which is my WAN.
I also have the vmbr1 bridge, containing the other interfaces enp3s0, enp4s0, enp5s0 as my LAN, this one serving as a "switch":
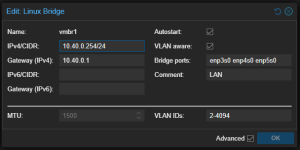
Here, in my vmbr1 bridge, I left the configuration that is being displayed, for passing my VLANs: VLAN aware activated and in VLAN IDs, I left the default space 2-4094 from Proxmox:
This is where my problem begins... My Windows computer is connected directly to the enp3s0 port of this bridge and my Unifi is connected to the enp4s0 port.
Since Unifi is prepared for VLANs, it can deliver the separate traffic as desired (of course, after configuring the segmented VLANs).
However, my Windows computer ends up receiving IPv6 broadcasts from the 3 networks I have (local network, IoT and guest), and it looks like this:
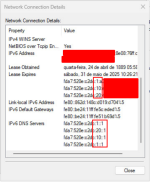
We have:
1 - Local network (this network does not have any VLAN tag, it is outside of any type of segregation)
10 - IoT network
20 - Guest network
I don't have a switch between my Windows computer and my Proxmox host.
Have you ever seen anything like this? Did I configure the host incorrectly?
To do this segregation, would I actually need to have a managed switch to separate this traffic?
I would appreciate any comments about this scenario... I've been testing various configurations and reading countless documents for 10 days, but none of them seem to help me.
First of all, I would like to thank you for your attention and apologize if there are any mistakes in English, since this is not my native language.
I am new to virtualized environments and have had a homelab at home for a few weeks.
I have about 4 virtual machines, running beautifully on my Proxmox host.
I have currently virtualized pfSense within my host and since then I have been using it as a router/firewall in my home, which has worked very well so far!
About 10 days ago, I decided to segment my guest and IoT network, since I have a Unifi and it is compatible with VLANs.
The problem with this is that according to the configuration I made, my 2 VLANs end up "leaking" tagged traffic to my untagged network.
Below, I will detail how my interfaces are configured.
Here, we have the interfaces as they are configured in my pfSense: WAN, LAN, NPt (this interface being ghost, being used only to obtain an IPv6 prefix from my ISP) and my VLAN interface:

Here, we have how my proxmox is configured.
I have the vmbr0 bridge that has the eno1 interface, which is my WAN.
I also have the vmbr1 bridge, containing the other interfaces enp3s0, enp4s0, enp5s0 as my LAN, this one serving as a "switch":

Here, in my vmbr1 bridge, I left the configuration that is being displayed, for passing my VLANs: VLAN aware activated and in VLAN IDs, I left the default space 2-4094 from Proxmox:

This is where my problem begins... My Windows computer is connected directly to the enp3s0 port of this bridge and my Unifi is connected to the enp4s0 port.
Since Unifi is prepared for VLANs, it can deliver the separate traffic as desired (of course, after configuring the segmented VLANs).
However, my Windows computer ends up receiving IPv6 broadcasts from the 3 networks I have (local network, IoT and guest), and it looks like this:

We have:
1 - Local network (this network does not have any VLAN tag, it is outside of any type of segregation)
10 - IoT network
20 - Guest network
I don't have a switch between my Windows computer and my Proxmox host.
Have you ever seen anything like this? Did I configure the host incorrectly?
To do this segregation, would I actually need to have a managed switch to separate this traffic?
I would appreciate any comments about this scenario... I've been testing various configurations and reading countless documents for 10 days, but none of them seem to help me.

