Hey all,
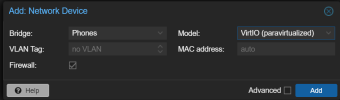
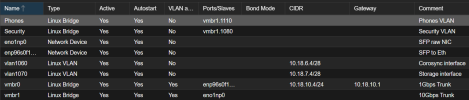
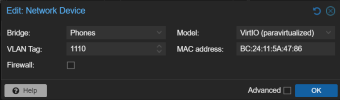
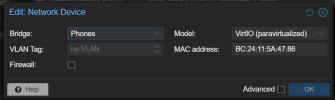
Been working on setting up some VLANs as bridges at the host level. Typically I simply add the NIC to the VM, then VLAN tag it there, however I want to try to add the VLAN to the host as a bridge, and pass tagged traffic through a bridge to the VM from there (kind of like VMWare). Firstly, is this even possible? Official documentation seems to indicate it is: https://pve.proxmox.com/wiki/Network_Configuration#sysadmin_network_vlan.
Secondly, I've got two configs, neither of which seem to work. Can someone help me determine if there's something wrong with my approach(es) and which is most correct? Ideally I'd use Config 1 because IMO it is the cleanest. Thanks in advance for any feedback.
Been working on setting up some VLANs as bridges at the host level. Typically I simply add the NIC to the VM, then VLAN tag it there, however I want to try to add the VLAN to the host as a bridge, and pass tagged traffic through a bridge to the VM from there (kind of like VMWare). Firstly, is this even possible? Official documentation seems to indicate it is: https://pve.proxmox.com/wiki/Network_Configuration#sysadmin_network_vlan.
Secondly, I've got two configs, neither of which seem to work. Can someone help me determine if there's something wrong with my approach(es) and which is most correct? Ideally I'd use Config 1 because IMO it is the cleanest. Thanks in advance for any feedback.
Code:
auto eno1np0
iface eno1np0 inet manual
#SFP raw NIC
auto vmbr1
iface vmbr1 inet manual
bridge-ports eno1np0
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
#10Gbps Trunk
auto Phones
iface Phones inet manual
bridge-ports vmbr1.1110
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 1110
vlan-id 1110
#Phones VLAN bridge
auto Security
iface Security inet manual
bridge-ports vmbr1.1080
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 1080
vlan-id 1080
#Security VLAN bridge
Code:
auto eno1np0
iface eno1np0 inet manual
#SFP raw NIC
auto vmbr1
iface vmbr1 inet manual
bridge-ports eno1np0
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
#10Gbps Trunk
auto vlan1110
iface vlan1110 inet manual
vlan-raw-device vmbr1
#Phones VLAN
auto Phones
iface Phones inet manual
bridge-ports vlan1110
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 1110
#Phones VLAN bridge
auto vlan1080
iface vlan1080 inet manual
vlan-raw-device vmbr1
#Security VLAN
auto Security
iface Security inet manual
bridge-ports vlan1080
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 1080
#Security VLAN bridge
Last edited: