Here are the top line facts:
I have found other qemu posts (not proxmox) where this host passtrough on win11 seems to cause issues.
Things i have tried:
I need a way to keep host CPU enabled and avoid the reboot loops.
OR
I need a way with a virtualized CPU type to not have the windows intel drivers fail
I realize not everyone has this issue so i wonder if it is something to do with the specifics of my cpu?
- I have i915 vGPU working on my host.
- I install a new win11 VM.
- I get the win11 VM working with VGPU
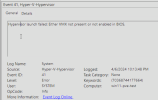
- at some point later on a reboot the Win11 machine goes into automatic repair (this seems to be time based, not due to windows updates, not installing anything, not changing anything
- if i set the CPU type to x86-64-v2-AES then the system boots...
- ...but this breaks vGPU with the dreaded code 43
I have found other qemu posts (not proxmox) where this host passtrough on win11 seems to cause issues.
Things i have tried:
- setting /sys/module/kvm/parameters/ignore_msrs = Y
- setting host,hidden=1
- tried this driver trick - works to get access to c:\ but no improvement
- various args in the vm conf
- re-installing win11 in fresh VM multiple times
- disabling network to stop updates
I need a way to keep host CPU enabled and avoid the reboot loops.
OR
I need a way with a virtualized CPU type to not have the windows intel drivers fail
I realize not everyone has this issue so i wonder if it is something to do with the specifics of my cpu?
-
Code:
root@pve1:/etc/pve/qemu-server# cat /proc/cpuinfo processor : 0 vendor_id : GenuineIntel cpu family : 6 model : 186 model name : 13th Gen Intel(R) Core(TM) i7-1360P stepping : 2 microcode : 0x410e cpu MHz : 691.790 cache size : 18432 KB physical id : 0 siblings : 16 core id : 0 cpu cores : 12 apicid : 0 initial apicid : 0 fpu : yes fpu_exception : yes cpuid level : 32 wp : yes flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall nx pdpe1gb rdtscp lm constant_tsc art arch_perfmon pebs bts rep_good nopl xtopology nonstop_tsc cpuid aperfmperf tsc_known_freq pni pclmulqdq dtes64 monitor ds_cpl vmx smx est tm2 ssse3 sdbg fma cx16 xtpr pdcm sse4_1 sse4_2 x2apic movbe popcnt tsc_deadline_timer aes xsave avx f16c rdrand lahf_lm abm 3dnowprefetch cpuid_fault epb ssbd ibrs ibpb stibp ibrs_enhanced tpr_shadow flexpriority ept vpid ept_ad fsgsbase tsc_adjust bmi1 avx2 smep bmi2 erms invpcid rdseed adx smap clflushopt clwb intel_pt sha_ni xsaveopt xsavec xgetbv1 xsaves split_lock_detect avx_vnni dtherm ida arat pln pts hwp hwp_notify hwp_act_window hwp_epp hwp_pkg_req hfi vnmi umip pku ospke waitpkg gfni vaes vpclmulqdq rdpid movdiri movdir64b fsrm md_clear serialize arch_lbr ibt flush_l1d arch_capabilities vmx flags : vnmi preemption_timer posted_intr invvpid ept_x_only ept_ad ept_1gb flexpriority apicv tsc_offset vtpr mtf vapic ept vpid unrestricted_guest vapic_reg vid ple shadow_vmcs ept_mode_based_exec tsc_scaling usr_wait_pause bugs : spectre_v1 spectre_v2 spec_store_bypass swapgs eibrs_pbrsb bogomips : 5222.40 clflush size : 64 cache_alignment : 64 address sizes : 39 bits physical, 48 bits virtual power management:
Last edited: