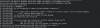
After upgrading to 5.3 I can no longer log into the gui, and have the following error in the syslog with each attempt:
previously was running 5.2, and followed the standard apt update, upgrade, dist-upgrade, reboot cycle.
Anything obvious I'm missing?
Code:
Mar 3 18:56:37 REDACTED pveproxy[3525]: dh params schmorp1539: failed to set DH parameters at /usr/share/perl5/PVE/APIServer/AnyEvent.pm line 622.
Mar 3 18:56:37 REDACTED pveproxy[3525]: problem with client 192.168.3.214; ssl3_ctx_ctrl: dh key too small
Mar 3 18:56:37 REDACTED pveproxy[3525]: dh params schmorp1539: failed to set DH parameters at /usr/share/perl5/PVE/APIServer/AnyEvent.pm line 622.
Mar 3 18:56:37 REDACTED pveproxy[3525]: problem with client 192.168.3.214; ssl3_ctx_ctrl: dh key too smallpreviously was running 5.2, and followed the standard apt update, upgrade, dist-upgrade, reboot cycle.
Anything obvious I'm missing?
Code:
# pveversion -v
proxmox-ve: 5.3-1 (running kernel: 4.15.18-11-pve)
pve-manager: 5.3-11 (running version: 5.3-11/d4907f84)
pve-kernel-4.15: 5.3-2
pve-kernel-4.15.18-11-pve: 4.15.18-34
pve-kernel-4.15.18-1-pve: 4.15.18-19
pve-kernel-4.15.17-1-pve: 4.15.17-9
corosync: 2.4.4-pve1
criu: 2.11.1-1~bpo90
glusterfs-client: 3.8.8-1
ksm-control-daemon: 1.2-2
libjs-extjs: 6.0.1-2
libpve-access-control: 5.1-3
libpve-apiclient-perl: 2.0-5
libpve-common-perl: 5.0-47
libpve-guest-common-perl: 2.0-20
libpve-http-server-perl: 2.0-11
libpve-storage-perl: 5.0-38
libqb0: 1.0.3-1~bpo9
lvm2: 2.02.168-pve6
lxc-pve: 3.1.0-3
lxcfs: 3.0.3-pve1
novnc-pve: 1.0.0-2
openvswitch-switch: 2.10.0+2018.08.28+git.8ca7c82b7d+ds1-10
proxmox-widget-toolkit: 1.0-22
pve-cluster: 5.0-33
pve-container: 2.0-34
pve-docs: 5.3-3
pve-edk2-firmware: 1.20181023-1
pve-firewall: 3.0-17
pve-firmware: 2.0-6
pve-ha-manager: 2.0-6
pve-i18n: 1.0-9
pve-libspice-server1: 0.14.1-2
pve-qemu-kvm: 2.12.1-2
pve-xtermjs: 3.10.1-1
qemu-server: 5.0-46
smartmontools: 6.5+svn4324-1
spiceterm: 3.0-5
vncterm: 1.5-3
zfsutils-linux: 0.7.12-pve1~bpo1