Hello everyone,
I am running two PMGs in a cluster and have been having problems receiving emails with node2 for some time.
The test from internet.nl claims that the PMG does not offer STARTTLS and does not test any further. The test from checktls.com, on the other hand, shows the following error:
I have gone through the confis of both servers several times and can't see any difference, especially as the two sync anyway.
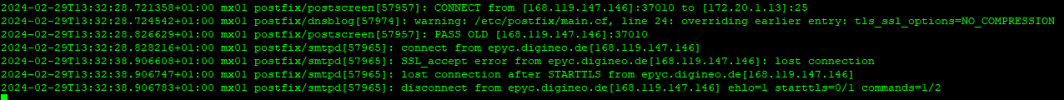
Unfortunately, I can't do anything with the error message.
I am running two PMGs in a cluster and have been having problems receiving emails with node2 for some time.
The test from internet.nl claims that the PMG does not offer STARTTLS and does not test any further. The test from checktls.com, on the other hand, shows the following error:
[000.000] Trying TLS on *******[1.2.3.4:25] (20) [000.099] Server answered [000.211] <‑‑ 220 nice.smtp.banner [000.211] We are allowed to connect [000.212] ‑‑> EHLO www12-azure.checktls.com [000.307] <‑‑ 250-nice.smtp.banner
250-PIPELINING
250-SIZE 25000000
250-ETRN
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-8BITMIME
250-SMTPUTF8
250 CHUNKING[000.308] We can use this server [000.308] TLS is an option on this server [000.308] ‑‑> STARTTLS [000.403] <‑‑ 220 2.0.0 Ready to start TLS [000.403] STARTTLS command works on this server [004.407] Cannot convert to SSL (reason: SSL wants a read first) [004.408] Note: This same test with Format set to "Debug" may show more [004.408] ‑‑> MAIL FROM:<test@checktls.com> [004.408] Read failed (reason: did not read) [004.408] ‑‑> QUIT [004.409] Read failed (reason: did not read)
I have gone through the confis of both servers several times and can't see any difference, especially as the two sync anyway.
Unfortunately, I can't do anything with the error message.