Hallo everyone,
I just installed last versione of PVS (4.2), and did an apt-get update/upgrade.
I created a test CT using Ubuntu 14.04 template downloaded from the web interface.
I did a setup of the new CT (100) using following network configuration
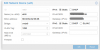
When I boot the CT 100 I receive an error message.
I tried from command line and set the debug level as follow:
# lxc-start -n 100 --logfile /tmp/errore --logpriority DEBUG -F
This is the error message i receive on stdout
# lxc-start -n 100 --logfile /tmp/errore --logpriority DEBUG -F
bridge 'vmbr0' does not exist
lxc-start: conf.c: run_buffer: 342 Script exited with status 2
lxc-start: conf.c: lxc_create_network: 3084 failed to create netdev
lxc-start: start.c: lxc_spawn: 954 failed to create the network
lxc-start: start.c: __lxc_start: 1211 failed to spawn '100'
lxc-start: lxc_start.c: main: 344 The container failed to start.
lxc-start: lxc_start.c: main: 348 Additional information can be obtained by setting the --logfile and --logpriority options.
#
and you can see the full log file:
lxc-start 1467985650.735 INFO lxc_start_ui - lxc_start.c:main:264 - using rcfile /var/lib/lxc/100/config
lxc-start 1467985650.735 WARN lxc_confile - confile.c:config_pivotdir:1817 - lxc.pivotdir is ignored. It will soon become an error.
lxc-start 1467985650.738 WARN lxc_cgmanager - cgmanager.c:cgm_get:994 - do_cgm_get exited with error
lxc-start 1467985650.739 INFO lxc_lsm - lsm/lsm.c:lsm_init:48 - LSM security driver AppArmor
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:324 - processing: .reject_force_umount # comment this to allow umount -f; not recommended.
arse_config_v2:324 - processing: .reject_force_umount # comment this to allow umount -f; not recommended.
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:426 - Adding native rule for reject_force_umount action 0
arse_config_v2:426 - Adding native rule for reject_force_umount action 0
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:216 - Setting seccomp rule to reject force umounts
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:429 - Adding compat rule for reject_force_umount action 0
arse_config_v2:429 - Adding compat rule for reject_force_umount action 0
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:216 - Setting seccomp rule to reject force umounts
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:324 - processing: .[all].
arse_config_v2:324 - processing: .[all].
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:324 - processing: .kexec_load errno 1.
arse_config_v2:324 - processing: .kexec_load errno 1.
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:426 - Adding native rule for kexec_load action 327681
arse_config_v2:426 - Adding native rule for kexec_load action 327681
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:429 - Adding compat rule for kexec_load action 327681
arse_config_v2:429 - Adding compat rule for kexec_load action 327681
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:324 - processing: .open_by_handle_at errno 1.
arse_config_v2:324 - processing: .open_by_handle_at errno 1.
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:426 - Adding native rule for open_by_handle_at action 327681
arse_config_v2:426 - Adding native rule for open_by_handle_at action 327681
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:429 - Adding compat rule for open_by_handle_at action 327681
arse_config_v2:429 - Adding compat rule for open_by_handle_at action 327681
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:324 - processing: .init_module errno 1.
arse_config_v2:324 - processing: .init_module errno 1.
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:426 - Adding native rule for init_module action 327681
arse_config_v2:426 - Adding native rule for init_module action 327681
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:429 - Adding compat rule for init_module action 327681
arse_config_v2:429 - Adding compat rule for init_module action 327681
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:324 - processing: .finit_module errno 1.
arse_config_v2:324 - processing: .finit_module errno 1.
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:426 - Adding native rule for finit_module action 327681
arse_config_v2:426 - Adding native rule for finit_module action 327681
lxc-start 1467985650.739 WARN lxc_seccomp - seccomp.c:do_resolve_add_rule:233 - Seccomp: got negative # for syscall: finit_module
lxc-start 1467985650.739 WARN lxc_seccomp - seccomp.c:do_resolve_add_rule:234 - This syscall will NOT be blacklisted
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:429 - Adding compat rule for finit_module action 327681
arse_config_v2:429 - Adding compat rule for finit_module action 327681
lxc-start 1467985650.739 WARN lxc_seccomp - seccomp.c:do_resolve_add_rule:233 - Seccomp: got negative # for syscall: finit_module
lxc-start 1467985650.739 WARN lxc_seccomp - seccomp.c:do_resolve_add_rule:234 - This syscall will NOT be blacklisted
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:324 - processing: .delete_module errno 1.
arse_config_v2:324 - processing: .delete_module errno 1.
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:426 - Adding native rule for delete_module action 327681
arse_config_v2:426 - Adding native rule for delete_module action 327681
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:429 - Adding compat rule for delete_module action 327681
arse_config_v2:429 - Adding compat rule for delete_module action 327681
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c arse_config_v2:436 - Merging in the compat seccomp ctx into the main one
arse_config_v2:436 - Merging in the compat seccomp ctx into the main one
lxc-start 1467985650.739 INFO lxc_conf - conf.c:run_script_argv:362 - Executing script '/usr/share/lxc/hooks/lxc-pve-prestart-hook' for container '100', config section 'lxc'
lxc-start 1467985652.310 DEBUG lxc_start - start.c:setup_signal_fd:264 - sigchild handler set
lxc-start 1467985652.311 DEBUG lxc_console - console.c:lxc_console_peer_default:500 - opening /dev/tty for console peer
lxc-start 1467985652.311 DEBUG lxc_console - console.c:lxc_console_peer_default:506 - using '/dev/tty' as console
lxc-start 1467985652.311 DEBUG lxc_console - console.c:lxc_console_sigwinch_init:179 - 12283 got SIGWINCH fd 9
lxc-start 1467985652.311 DEBUG lxc_console - console.c:lxc_console_winsz:88 - set winsz dstfd:6 cols:202 rows:67
lxc-start 1467985652.311 INFO lxc_start - start.c:lxc_init:460 - '100' is initialized
lxc-start 1467985652.312 DEBUG lxc_start - start.c:__lxc_start:1184 - Not dropping cap_sys_boot or watching utmp
lxc-start 1467985652.315 INFO lxc_conf - conf.c:run_script:412 - Executing script '/usr/share/lxc/lxcnetaddbr' for container '100', config section 'net'
lxc-start 1467985653.042 ERROR lxc_conf - conf.c:run_buffer:342 - Script exited with status 2
lxc-start 1467985653.085 ERROR lxc_conf - conf.c:lxc_create_network:3084 - failed to create netdev
lxc-start 1467985653.085 ERROR lxc_start - start.c:lxc_spawn:954 - failed to create the network
lxc-start 1467985653.085 ERROR lxc_start - start.c:__lxc_start:1211 - failed to spawn '100'
lxc-start 1467985653.085 INFO lxc_conf - conf.c:run_script_argv:362 - Executing script '/usr/share/lxc/hooks/lxc-pve-poststop-hook' for container '100', config section 'lxc'
lxc-start 1467985654.753 INFO lxc_conf - conf.c:run_script_argv:362 - Executing script '/usr/share/lxcfs/lxc.reboot.hook' for container '100', config section 'lxc'
lxc-start 1467985655.259 ERROR lxc_start_ui - lxc_start.c:main:344 - The container failed to start.
lxc-start 1467985655.259 ERROR lxc_start_ui - lxc_start.c:main:348 - Additional information can be obtained by setting the --logfile and --logpriority options.
Follow pve version
# pveversion
pve-manager/4.2-2/725d76f0 (running kernel: 4.4.6-1-pve)
My network configuration
# cat /etc/network/interfaces
auto lo
iface lo inet loopback
iface eth0 inet manual
iface eth1 inet manual
iface eth2 inet manual
iface eth3 inet manual
auto bond0
iface bond0 inet manual
slaves eth2 eth3
bond_miimon 100
bond-miimon 100
bond_mode active-backup
bond-mode active-backup
auto bond0.1064
iface bond0.1064 inet static
address X.X.X.X
netmask 255.255.255.192
gateway X.X.X.X
vlan_raw_device bond0
dns-nameservers X.X.X.X X.X.X.X
dns-search enavsoc.dev
auto vmbr0
iface vmbr0 inet static
bridge_ports bond0
bridge_stp off
bridge_fd 0
Hope someone can help, tks
Giovanni
I just installed last versione of PVS (4.2), and did an apt-get update/upgrade.
I created a test CT using Ubuntu 14.04 template downloaded from the web interface.
I did a setup of the new CT (100) using following network configuration

When I boot the CT 100 I receive an error message.
I tried from command line and set the debug level as follow:
# lxc-start -n 100 --logfile /tmp/errore --logpriority DEBUG -F
This is the error message i receive on stdout
# lxc-start -n 100 --logfile /tmp/errore --logpriority DEBUG -F
bridge 'vmbr0' does not exist
lxc-start: conf.c: run_buffer: 342 Script exited with status 2
lxc-start: conf.c: lxc_create_network: 3084 failed to create netdev
lxc-start: start.c: lxc_spawn: 954 failed to create the network
lxc-start: start.c: __lxc_start: 1211 failed to spawn '100'
lxc-start: lxc_start.c: main: 344 The container failed to start.
lxc-start: lxc_start.c: main: 348 Additional information can be obtained by setting the --logfile and --logpriority options.
#
and you can see the full log file:
lxc-start 1467985650.735 INFO lxc_start_ui - lxc_start.c:main:264 - using rcfile /var/lib/lxc/100/config
lxc-start 1467985650.735 WARN lxc_confile - confile.c:config_pivotdir:1817 - lxc.pivotdir is ignored. It will soon become an error.
lxc-start 1467985650.738 WARN lxc_cgmanager - cgmanager.c:cgm_get:994 - do_cgm_get exited with error
lxc-start 1467985650.739 INFO lxc_lsm - lsm/lsm.c:lsm_init:48 - LSM security driver AppArmor
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:216 - Setting seccomp rule to reject force umounts
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:216 - Setting seccomp rule to reject force umounts
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 WARN lxc_seccomp - seccomp.c:do_resolve_add_rule:233 - Seccomp: got negative # for syscall: finit_module
lxc-start 1467985650.739 WARN lxc_seccomp - seccomp.c:do_resolve_add_rule:234 - This syscall will NOT be blacklisted
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 WARN lxc_seccomp - seccomp.c:do_resolve_add_rule:233 - Seccomp: got negative # for syscall: finit_module
lxc-start 1467985650.739 WARN lxc_seccomp - seccomp.c:do_resolve_add_rule:234 - This syscall will NOT be blacklisted
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_seccomp - seccomp.c
lxc-start 1467985650.739 INFO lxc_conf - conf.c:run_script_argv:362 - Executing script '/usr/share/lxc/hooks/lxc-pve-prestart-hook' for container '100', config section 'lxc'
lxc-start 1467985652.310 DEBUG lxc_start - start.c:setup_signal_fd:264 - sigchild handler set
lxc-start 1467985652.311 DEBUG lxc_console - console.c:lxc_console_peer_default:500 - opening /dev/tty for console peer
lxc-start 1467985652.311 DEBUG lxc_console - console.c:lxc_console_peer_default:506 - using '/dev/tty' as console
lxc-start 1467985652.311 DEBUG lxc_console - console.c:lxc_console_sigwinch_init:179 - 12283 got SIGWINCH fd 9
lxc-start 1467985652.311 DEBUG lxc_console - console.c:lxc_console_winsz:88 - set winsz dstfd:6 cols:202 rows:67
lxc-start 1467985652.311 INFO lxc_start - start.c:lxc_init:460 - '100' is initialized
lxc-start 1467985652.312 DEBUG lxc_start - start.c:__lxc_start:1184 - Not dropping cap_sys_boot or watching utmp
lxc-start 1467985652.315 INFO lxc_conf - conf.c:run_script:412 - Executing script '/usr/share/lxc/lxcnetaddbr' for container '100', config section 'net'
lxc-start 1467985653.042 ERROR lxc_conf - conf.c:run_buffer:342 - Script exited with status 2
lxc-start 1467985653.085 ERROR lxc_conf - conf.c:lxc_create_network:3084 - failed to create netdev
lxc-start 1467985653.085 ERROR lxc_start - start.c:lxc_spawn:954 - failed to create the network
lxc-start 1467985653.085 ERROR lxc_start - start.c:__lxc_start:1211 - failed to spawn '100'
lxc-start 1467985653.085 INFO lxc_conf - conf.c:run_script_argv:362 - Executing script '/usr/share/lxc/hooks/lxc-pve-poststop-hook' for container '100', config section 'lxc'
lxc-start 1467985654.753 INFO lxc_conf - conf.c:run_script_argv:362 - Executing script '/usr/share/lxcfs/lxc.reboot.hook' for container '100', config section 'lxc'
lxc-start 1467985655.259 ERROR lxc_start_ui - lxc_start.c:main:344 - The container failed to start.
lxc-start 1467985655.259 ERROR lxc_start_ui - lxc_start.c:main:348 - Additional information can be obtained by setting the --logfile and --logpriority options.
Follow pve version
# pveversion
pve-manager/4.2-2/725d76f0 (running kernel: 4.4.6-1-pve)
My network configuration
# cat /etc/network/interfaces
auto lo
iface lo inet loopback
iface eth0 inet manual
iface eth1 inet manual
iface eth2 inet manual
iface eth3 inet manual
auto bond0
iface bond0 inet manual
slaves eth2 eth3
bond_miimon 100
bond-miimon 100
bond_mode active-backup
bond-mode active-backup
auto bond0.1064
iface bond0.1064 inet static
address X.X.X.X
netmask 255.255.255.192
gateway X.X.X.X
vlan_raw_device bond0
dns-nameservers X.X.X.X X.X.X.X
dns-search enavsoc.dev
auto vmbr0
iface vmbr0 inet static
bridge_ports bond0
bridge_stp off
bridge_fd 0
Hope someone can help, tks
Giovanni

