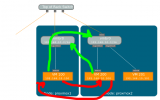
Hello everyone, I need help setting up a network between three proxmox servers. I'm new to this.
I have three servers. Each of them has two network cards, the first looks at the Internet, and the second connects the other servers via a switch.
I need the vm and ct to be visible to each other from the second network interface where only the proxmox servers are connected
I have three servers. Each of them has two network cards, the first looks at the Internet, and the second connects the other servers via a switch.
I need the vm and ct to be visible to each other from the second network interface where only the proxmox servers are connected