I'm trying to figure out how to secure access to the web GUI i.e. how to setup networking both physical and logical. I've read all the blogs I could find on Google, posts on reddit and these forums and have read all relevant sections in the documentation (everything multiple times). However, I'm still unsure of how things work or what I should do. Not being well versed in networking and proxies doesn't help in solving this puzzle.
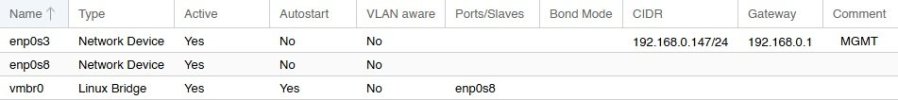
In my mind, the web GUI should live on a management network. Specifically on an OOB management network. However, if I put it there, since that network doesn't have access to the internet, I won't be able to update Proxmox.
It seems most people are either using pveproxy or Nginx reverse proxy. Not sure how those solve the problem to be honest. Why some people use one or the other for example. Everywhere I look, it seems like proxies are for internet facing applications and Proxmox isn't internet facing.
In my mind, the web GUI should live on a management network. Specifically on an OOB management network. However, if I put it there, since that network doesn't have access to the internet, I won't be able to update Proxmox.
It seems most people are either using pveproxy or Nginx reverse proxy. Not sure how those solve the problem to be honest. Why some people use one or the other for example. Everywhere I look, it seems like proxies are for internet facing applications and Proxmox isn't internet facing.
Last edited: