Hi, I am new to Proxmox. I just installed it in my home server and played around with it a bit, created a few containers, changed the network configuration. I want to know if the network configuration that I am planning makes sense and it is safe, or if there is a better way to do what I want to do.
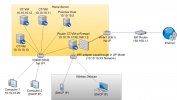
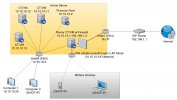
I am installing Proxmox in my home server. The only other physical devices are the ISP router and other consumer devices that will get an IP through DHCP. In the future, I want to run another Proxmox in a VPS as a reverse proxy for the services in my home server, so my home ISP IP is not exposed, but this is not my concern now. The Proxmox in my home server should run a container that will act as a router.
My home server has 3 network connections, 2 wired ethernet and one wireless. One of the wired ethernet will be for the host. The other wired ethernet will be for the router container and will be connected to the ISP router, to the internet. The wireless device will be for the router container and will act as an wireless AP.
I have created a diagram because writing it would be long and tedios to read (some doubts after the diagram):
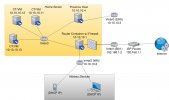
1. Is this the best way to run a router as a container inside a Proxmox host. I would prefer for the router to be a container/VM and not the host itself.
2. As I understand, the host needs to have its own ethernet interface, so that if the router container has an issue, I can still access the host. Since I have physical access to the machine, I will leave this ethernet (eth0 in the diagram) disconnected, but if the router container stops responding, I could connect to the host by setting up a static IP 10.10.10.XX in my laptop and connecting it to eth0. Is this correct?
3. Why do some linux bridges need their own IP?
I am installing Proxmox in my home server. The only other physical devices are the ISP router and other consumer devices that will get an IP through DHCP. In the future, I want to run another Proxmox in a VPS as a reverse proxy for the services in my home server, so my home ISP IP is not exposed, but this is not my concern now. The Proxmox in my home server should run a container that will act as a router.
My home server has 3 network connections, 2 wired ethernet and one wireless. One of the wired ethernet will be for the host. The other wired ethernet will be for the router container and will be connected to the ISP router, to the internet. The wireless device will be for the router container and will act as an wireless AP.
I have created a diagram because writing it would be long and tedios to read (some doubts after the diagram):

1. Is this the best way to run a router as a container inside a Proxmox host. I would prefer for the router to be a container/VM and not the host itself.
2. As I understand, the host needs to have its own ethernet interface, so that if the router container has an issue, I can still access the host. Since I have physical access to the machine, I will leave this ethernet (eth0 in the diagram) disconnected, but if the router container stops responding, I could connect to the host by setting up a static IP 10.10.10.XX in my laptop and connecting it to eth0. Is this correct?
3. Why do some linux bridges need their own IP?