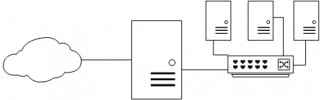
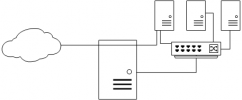
So, i'm running into a issue with setting up. I have eno1 plugged into that is going into the datacenters switch. vmbr is set with the routed block and the gateway being .142 but as I am looking at this is its showing .143 in which is incorrect but on proxmox gui it shows .142. Im trying to route out from one vm to the public internet with vmbr1 to bridge to vmbr0 to reach out to the world but having trouble.
root@fiendserver:/# ip route
default via xxx.71.205.142 dev vmbr0 onlink
192.168.10.0/24 dev vmbr1 proto kernel scope link src 192.168.10.100
207.71.205.136/29 dev vmbr0 proto kernel scope link src xxx.71.205.138
root@fiendserver:/#
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master vmbr0 state UP group default qlen 1000
link/ether 00:25:64:fd:2f:2d brd ff:ff:ff:ff:ff:ff
3: eno2: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 00:25:64:fd:2f:2f brd ff:ff:ff:ff:ff:ff
4: eno3: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 00:25:64:fd:2f:31 brd ff:ff:ff:ff:ff:ff
5: eno4: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 00:25:64:fd:2f:33 brd ff:ff:ff:ff:ff:ff
6: vmbr0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 00:25:64:fd:2f:2d brd ff:ff:ff:ff:ff:ff
inet xxx.71.205.138/29 brd xxx.71.205.143 scope global vmbr0
valid_lft forever preferred_lft forever
inet6 fe80::225:64ff:fefd:2f2d/64 scope link
valid_lft forever preferred_lft forever
7: vmbr1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 06:42:f8:95:94:d5 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.100/24 brd 192.168.10.255 scope global vmbr1
valid_lft forever preferred_lft forever
inet6 fe80::b4c4:c6ff:fe23:131c/64 scope link
valid_lft forever preferred_lft forever
8: tap100i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master fwbr100i0 state UNKNOWN group default qlen 1000
link/ether 6a:6f:41:39:b6:6e brd ff:ff:ff:ff:ff:ff
9: fwbr100i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 7a:15:6a:92:42:13 brd ff:ff:ff:ff:ff:ff
10: fwpr100p0@fwln100i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master vmbr1 state UP group default qlen 1000
link/ether 06:42:f8:95:94:d5 brd ff:ff:ff:ff:ff:ff
11: fwln100i0@fwpr100p0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master fwbr100i0 state UP group default qlen 1000
link/ether 7a:15:6a:92:42:13 brd ff:ff:ff:ff:ff:ff
root@fiendserver:/#
root@fiendserver:/# ip route
default via xxx.71.205.142 dev vmbr0 onlink
192.168.10.0/24 dev vmbr1 proto kernel scope link src 192.168.10.100
207.71.205.136/29 dev vmbr0 proto kernel scope link src xxx.71.205.138
root@fiendserver:/#
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master vmbr0 state UP group default qlen 1000
link/ether 00:25:64:fd:2f:2d brd ff:ff:ff:ff:ff:ff
3: eno2: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 00:25:64:fd:2f:2f brd ff:ff:ff:ff:ff:ff
4: eno3: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 00:25:64:fd:2f:31 brd ff:ff:ff:ff:ff:ff
5: eno4: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 00:25:64:fd:2f:33 brd ff:ff:ff:ff:ff:ff
6: vmbr0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 00:25:64:fd:2f:2d brd ff:ff:ff:ff:ff:ff
inet xxx.71.205.138/29 brd xxx.71.205.143 scope global vmbr0
valid_lft forever preferred_lft forever
inet6 fe80::225:64ff:fefd:2f2d/64 scope link
valid_lft forever preferred_lft forever
7: vmbr1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 06:42:f8:95:94:d5 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.100/24 brd 192.168.10.255 scope global vmbr1
valid_lft forever preferred_lft forever
inet6 fe80::b4c4:c6ff:fe23:131c/64 scope link
valid_lft forever preferred_lft forever
8: tap100i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master fwbr100i0 state UNKNOWN group default qlen 1000
link/ether 6a:6f:41:39:b6:6e brd ff:ff:ff:ff:ff:ff
9: fwbr100i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 7a:15:6a:92:42:13 brd ff:ff:ff:ff:ff:ff
10: fwpr100p0@fwln100i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master vmbr1 state UP group default qlen 1000
link/ether 06:42:f8:95:94:d5 brd ff:ff:ff:ff:ff:ff
11: fwln100i0@fwpr100p0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master fwbr100i0 state UP group default qlen 1000
link/ether 7a:15:6a:92:42:13 brd ff:ff:ff:ff:ff:ff
root@fiendserver:/#
Last edited: