Hi,
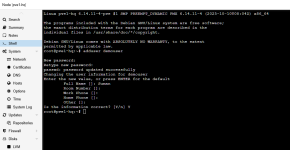
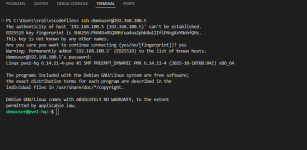
Is it OK to restrict SSH PermitRootLogin to only PVE IP? Would this have an impact on how PVE works?
The goal is to prevent direct root connection via SSH from the rest of the network.
Is it OK to restrict SSH PermitRootLogin to only PVE IP? Would this have an impact on how PVE works?
The goal is to prevent direct root connection via SSH from the rest of the network.
Code:
Match User root Address 1.2.3.*
PermitRootLogin yes
Match all