Hi everyone,
I've searched quite a bit surrounding this question, but my apologies in advance if I've missed something. I will try to recap what I've attempted, but I've been working on this for quite some time, I likely have missed some things I've tried.
I would like to create a "wild west" network bridge that is completely unfiltered between three VMs. Proxmox has sane defaults that are awesome, except for this use-case. Hahah. And I can't seem to figure out how to disable them.
I was able to do this in VirtualBox, screenshot of some SYN attacks between a 3 VM network, in this case, 192.168.57.5 and .3:
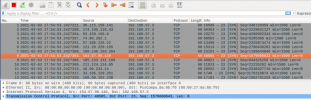
Naturally, this traffic is filtered by Proxmox (as it should be) for a variety of reasons, first, these are spoofed source IPs, and this is a SYN flood.
Doing the exact same thing in a Proxmox build of the same 3 VM environment (different IP subnet though), from 10.1.0.3 to .1:
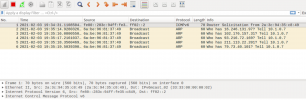
All I see is the ARP data. Something is filtering everything else. I've attempted to completely disable the PVE-Firewall via the service, clearing IP Tables, clearing EB Tables, etc. I see there are a number of SYN-related rules by default, so I was sure this would fix the issue. Sadly, it has not. I've also disabled all firewalling I can find in the UI, just to be sure.
I've seen similar behavior with other tests as well, the traffic shown on Proxmox is far less than what is shown on a similar configuration within VirtualBox. (Missing all traffic that isn't an IP Address on the subnet, missing a lot of the SYN traffic, etc.)
In Proxmox, I've set the following:
/etc/network/interfaces
From this config, you can see that I have set promiscuous mode on for the physical host interfaces, and bridge-ageing 0 on the Linux virtual bridges to make them act as a hub (all traffic to all ports). This definitely helped, as previously no traffic was showing up on the port I was monitoring.
I have tried the e1000, and virtio-net drivers. I've also tried setting a VLAN for the ports and enabling "VLAN Aware" on the bridge, as I read that this would help on some random blog. I've also poked around with OpenVSwitch, to no avail.
I have also tried the following:
This was in an attempt to disable netfiltering on the bridges. Confirming that it applied, but still doesn't do what I want:
How can one disable all of the "smarts" built into a bridge on Proxmox? I can't seem to figure it out.
I am attempting to avoid using a SPAN (mirror) port on the OpenVSwitch for... reasons. But I am thinking that may be the only way around this.
Thanks!!
I've searched quite a bit surrounding this question, but my apologies in advance if I've missed something. I will try to recap what I've attempted, but I've been working on this for quite some time, I likely have missed some things I've tried.
I would like to create a "wild west" network bridge that is completely unfiltered between three VMs. Proxmox has sane defaults that are awesome, except for this use-case. Hahah. And I can't seem to figure out how to disable them.
I was able to do this in VirtualBox, screenshot of some SYN attacks between a 3 VM network, in this case, 192.168.57.5 and .3:

Naturally, this traffic is filtered by Proxmox (as it should be) for a variety of reasons, first, these are spoofed source IPs, and this is a SYN flood.
Doing the exact same thing in a Proxmox build of the same 3 VM environment (different IP subnet though), from 10.1.0.3 to .1:

All I see is the ARP data. Something is filtering everything else. I've attempted to completely disable the PVE-Firewall via the service, clearing IP Tables, clearing EB Tables, etc. I see there are a number of SYN-related rules by default, so I was sure this would fix the issue. Sadly, it has not. I've also disabled all firewalling I can find in the UI, just to be sure.
I've seen similar behavior with other tests as well, the traffic shown on Proxmox is far less than what is shown on a similar configuration within VirtualBox. (Missing all traffic that isn't an IP Address on the subnet, missing a lot of the SYN traffic, etc.)
In Proxmox, I've set the following:
/etc/network/interfaces
Code:
auto lo
iface lo inet loopback
iface enp0s31f6 inet manual
up /usr/sbin/ip link set $IFACE promisc on
iface enp2s0 inet manual
up /usr/sbin/ip link set $IFACE promisc on
auto vmbr0
iface vmbr0 inet static
address x.x.x.x/22
gateway x.x.x.x
bridge-ports enp0s31f6
bridge-stp off
bridge-fd 0
bridge-ageing 0
auto vmbr1
iface vmbr1 inet static
address 10.1.0.199/16
bridge-ports none
bridge-stp off
bridge-fd 0
bridge-ageing 0From this config, you can see that I have set promiscuous mode on for the physical host interfaces, and bridge-ageing 0 on the Linux virtual bridges to make them act as a hub (all traffic to all ports). This definitely helped, as previously no traffic was showing up on the port I was monitoring.
Code:
root@proxmox0:/etc/network# ebtables -L
Bridge table: filter
Bridge chain: INPUT, entries: 0, policy: ACCEPT
Bridge chain: FORWARD, entries: 0, policy: ACCEPT
Bridge chain: OUTPUT, entries: 0, policy: ACCEPT
root@proxmox0:/etc/network# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destinationI have tried the e1000, and virtio-net drivers. I've also tried setting a VLAN for the ports and enabling "VLAN Aware" on the bridge, as I read that this would help on some random blog. I've also poked around with OpenVSwitch, to no avail.
I have also tried the following:
Code:
echo 0 | tee /proc/sys/net/bridge/bridge-nf-call-arptables
echo 0 | tee /proc/sys/net/bridge/bridge-nf-call-iptables
echo 0 | tee /proc/sys/net/bridge/bridge-nf-call-ip6tablesThis was in an attempt to disable netfiltering on the bridges. Confirming that it applied, but still doesn't do what I want:
Code:
root@proxmox0:/etc/network# sysctl -a | grep bridge-nf
net.bridge.bridge-nf-call-arptables = 0
net.bridge.bridge-nf-call-ip6tables = 0
net.bridge.bridge-nf-call-iptables = 0
net.bridge.bridge-nf-filter-pppoe-tagged = 0
net.bridge.bridge-nf-filter-vlan-tagged = 0
net.bridge.bridge-nf-pass-vlan-input-dev = 0How can one disable all of the "smarts" built into a bridge on Proxmox? I can't seem to figure it out.
I am attempting to avoid using a SPAN (mirror) port on the OpenVSwitch for... reasons. But I am thinking that may be the only way around this.
Thanks!!

