proxmox 7 update to 8 error
- Thread starter tayra
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
The error message is complaining about theWhat's wrong?
proxmox-ve package, not the pve-manager.Please show output of:
Code:
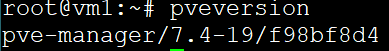
pveversion -v | grep "proxmox-ve"Please share all the command outputs (in code blocks).pve7to8is not meant to upgrade. Use the GUI orpveupdate && pveupgradefor that.
Code:
= CHECKING VERSION INFORMATION FOR PVE PACKAGES =
Checking for package updates..
[33mWARN: updates for the following packages are available:
libcups2, libcurl4, libpam-runtime, krb5-locales, libgssapi-krb5-2, libcurl3-gnutls, openssh-client, libjs-bootstrap, tzdata, libtasn1-6, ssh, xsltproc, libcap2-bin, xxd, libexpat1, vim-common, libfreetype6, libpve-guest-common-perl, openssh-server, libkrb5support0, libbpf0, libfastjson4, libxml2, fonts-glyphicons-halflings, wget, proxmox-ve, proxmox-kernel-helper, libpython3.9-stdlib, python3-pkg-resources, libcap2, libc6, locales, libkrb5-3, libpam-modules, qemu-server, libpython3.9, vim-tiny, libk5crypto3, libsndfile1, login, gnutls-bin, libxslt1.1, libunbound8, distro-info-data, libpam-modules-bin, uidmap, libglib2.0-0, libssl1.1, pve-manager, openssh-sftp-server, libpam0g, libc-l10n, libc-bin, librabbitmq4, libgnutls30, curl, libjson-xs-perl, libpython3.9-minimal, python3.9, libgnutlsxx28, libicu67, libgnutls-dane0, pve-kernel-helper, openssl, python3.9-minimal, passwd
[0m
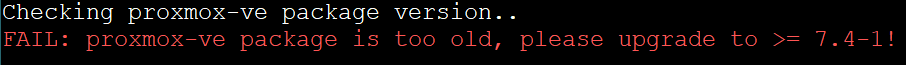
Checking proxmox-ve package version..
[1;31mFAIL: proxmox-ve package is too old, please upgrade to >= 7.4-1!
[0m
Checking running kernel version..
[32mPASS: running kernel '5.15.158-2-pve' is considered suitable for upgrade.
[0m
= CHECKING CLUSTER HEALTH/SETTINGS =
[32mPASS: systemd unit 'pve-cluster.service' is in state 'active'
[0m[32mPASS: systemd unit 'corosync.service' is in state 'active'
[0m[32mPASS: Cluster Filesystem is quorate.
[0m
Analzying quorum settings and state..
INFO: configured votes - nodes: 5
[0mINFO: configured votes - qdevice: 0
[0mINFO: current expected votes: 5
[0mINFO: current total votes: 5
[0m
Checking nodelist entries..
[32mPASS: nodelist settings OK
[0m
Checking totem settings..
[32mPASS: totem settings OK
[0m
INFO: run 'pvecm status' to get detailed cluster status..
[0m
= CHECKING HYPER-CONVERGED CEPH STATUS =
SKIP: no hyper-converged ceph setup detected!
[0m
= CHECKING CONFIGURED STORAGES =
[32mPASS: storage 'ReadyNAS' enabled and active.
[0mSKIP: storage 'b81' disabled.
[0mSKIP: storage 'b82' disabled.
[0m[32mPASS: storage 'd1_1' enabled and active.
[0mSKIP: storage 'd2_1' disabled.
[0m[32mPASS: storage 'd4' enabled and active.
[0mSKIP: storage 'd4_1' disabled.
[0mSKIP: storage 'f2_1' disabled.
[0m[32mPASS: storage 'f8' enabled and active.
[0mSKIP: storage 'local' disabled.
[0mSKIP: storage 'local-lvm' disabled.
[0m[32mPASS: storage 'nas4md5' enabled and active.
[0m[32mPASS: storage 'nas6' enabled and active.
[0mSKIP: storage 'raid1-2tb' disabled.
[0mSKIP: storage 'vd8tb' disabled.
[0mINFO: Checking storage content type configuration..
[0m[32mPASS: no storage content problems found
[0m[32mPASS: no storage re-uses a directory for multiple content types.
[0m
= MISCELLANEOUS CHECKS =
INFO: Checking common daemon services..
[0m[32mPASS: systemd unit 'pveproxy.service' is in state 'active'
[0m[32mPASS: systemd unit 'pvedaemon.service' is in state 'active'
[0m[32mPASS: systemd unit 'pvescheduler.service' is in state 'active'
[0m[32mPASS: systemd unit 'pvestatd.service' is in state 'active'
[0mINFO: Checking for supported & active NTP service..
[0m[33mWARN: systemd-timesyncd is not the best choice for time-keeping on servers, due to only applying updates on boot.
While not necessary for the upgrade it's recommended to use one of:
* chrony (Default in new Proxmox VE installations)
* ntpsec
* openntpd
[0mINFO: Checking for running guests..
[0m[33mWARN: 7 running guest(s) detected - consider migrating or stopping them.
[0mINFO: Checking if the local node's hostname 'vm1' is resolvable..
[0mINFO: Checking if resolved IP is configured on local node..
[0m[32mPASS: Resolved node IP '192.168.2.120' configured and active on single interface.
[0mINFO: Check node certificate's RSA key size
[0m[32mPASS: Certificate 'pve-root-ca.pem' passed Debian Busters (and newer) security level for TLS connections (4096 >= 2048)
[0m[32mPASS: Certificate 'pve-ssl.pem' passed Debian Busters (and newer) security level for TLS connections (2048 >= 2048)
[0mINFO: Checking backup retention settings..
[0m[32mPASS: no backup retention problems found.
[0mINFO: checking CIFS credential location..
[0m[32mPASS: no CIFS credentials at outdated location found.
[0mINFO: Checking permission system changes..
[0mINFO: Checking custom role IDs for clashes with new 'PVE' namespace..
[0m[32mPASS: no custom roles defined, so no clash with 'PVE' role ID namespace enforced in Proxmox VE 8
[0mINFO: Checking if LXCFS is running with FUSE3 library, if already upgraded..
[0mSKIP: not yet upgraded, no need to check the FUSE library version LXCFS uses
[0mINFO: Checking node and guest description/note length..
[0m[32mPASS: All node config descriptions fit in the new limit of 64 KiB
[0m[32mPASS: All guest config descriptions fit in the new limit of 8 KiB
[0mINFO: Checking container configs for deprecated lxc.cgroup entries
[0m[32mPASS: No legacy 'lxc.cgroup' keys found.
[0mINFO: Checking if the suite for the Debian security repository is correct..
[0m[32mPASS: found no suite mismatch
[0mINFO: Checking for existence of NVIDIA vGPU Manager..
[0m[32mPASS: No NVIDIA vGPU Service found.
[0mINFO: Checking bootloader configuration...
[0mSKIP: System booted in legacy-mode - no need for additional packages
[0mINFO: Check for dkms modules...
[0mSKIP: could not get dkms status
[0mSKIP: NOTE: Expensive checks, like CT cgroupv2 compat, not performed without '--full' parameter
[0m
= SUMMARY =
TOTAL: 47
[32mPASSED: 29
[0mSKIPPED: 14
[33mWARNINGS: 3
[0m[1;31mFAILURES: 1
[0m[1;31m
ATTENTION: Please check the output for detailed information!
[0m[1;31mTry to solve the problems one at a time and then run this checklist tool again.
[0mI meant the commands I shared above.
Code:
#apt policy proxmox-ve
proxmox-ve:
Installed: 7.3-1
Candidate: 7.4-1
Version table:
7.4-1 500
500 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 Packages
*** 7.3-1 500
500 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 Packages
100 /var/lib/dpkg/status
7.2-1 500
500 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 Packages
7.1-2 500
500 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 Packages
7.1-1 500
500 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 Packages
7.0-2 500
500 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 Packages
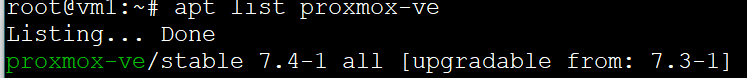
Code:
#apt list proxmox-ve
Listing...
proxmox-ve/stable 7.4-1 all [upgradable from: 7.3-1]
Code:
#apt list --upgradable
Listing...
curl/oldoldstable-security 7.74.0-1.3+deb11u15 amd64 [upgradable from: 7.74.0-1.3+deb11u14]
distro-info-data/oldoldstable-security 0.51+deb11u9 all [upgradable from: 0.51+deb11u7]
fonts-glyphicons-halflings/oldoldstable-security 1.009~3.4.1+dfsg-2+deb11u2 all [upgradable from: 1.009~3.4.1+dfsg-2]
gnutls-bin/oldoldstable-security 3.7.1-5+deb11u8 amd64 [upgradable from: 3.7.1-5+deb11u6]
krb5-locales/oldoldstable-security 1.18.3-6+deb11u7 all [upgradable from: 1.18.3-6+deb11u5]
libbpf0/oldoldstable-security 1:0.3-2+deb11u1 amd64 [upgradable from: 1:0.3-2]
libc-bin/oldoldstable-security 2.31-13+deb11u13 amd64 [upgradable from: 2.31-13+deb11u11]
libc-l10n/oldoldstable-security 2.31-13+deb11u13 all [upgradable from: 2.31-13+deb11u11]
libc6/oldoldstable-security 2.31-13+deb11u13 amd64 [upgradable from: 2.31-13+deb11u11]
libcap2-bin/oldoldstable-security 1:2.44-1+deb11u1 amd64 [upgradable from: 1:2.44-1]
libcap2/oldoldstable-security 1:2.44-1+deb11u1 amd64 [upgradable from: 1:2.44-1]
libcups2/oldoldstable-security 2.3.3op2-3+deb11u10 amd64 [upgradable from: 2.3.3op2-3+deb11u9]
libcurl3-gnutls/oldoldstable-security 7.74.0-1.3+deb11u15 amd64 [upgradable from: 7.74.0-1.3+deb11u14]
libcurl4/oldoldstable-security 7.74.0-1.3+deb11u15 amd64 [upgradable from: 7.74.0-1.3+deb11u14]
libexpat1/oldoldstable-security 2.2.10-2+deb11u7 amd64 [upgradable from: 2.2.10-2+deb11u6]
libfastjson4/oldoldstable-security 0.99.9-1+deb11u1 amd64 [upgradable from: 0.99.9-1]
libfreetype6/oldoldstable-security 2.10.4+dfsg-1+deb11u2 amd64 [upgradable from: 2.10.4+dfsg-1+deb11u1]
libglib2.0-0/oldoldstable-security 2.66.8-1+deb11u6 amd64 [upgradable from: 2.66.8-1+deb11u5]
libgnutls-dane0/oldoldstable-security 3.7.1-5+deb11u8 amd64 [upgradable from: 3.7.1-5+deb11u6]
libgnutls30/oldoldstable-security 3.7.1-5+deb11u8 amd64 [upgradable from: 3.7.1-5+deb11u6]
libgnutlsxx28/oldoldstable-security 3.7.1-5+deb11u8 amd64 [upgradable from: 3.7.1-5+deb11u6]
libgssapi-krb5-2/oldoldstable-security 1.18.3-6+deb11u7 amd64 [upgradable from: 1.18.3-6+deb11u5]
libicu67/oldoldstable-security 67.1-7+deb11u1 amd64 [upgradable from: 67.1-7]
libjs-bootstrap/oldoldstable-security 3.4.1+dfsg-2+deb11u2 all [upgradable from: 3.4.1+dfsg-2]
libjson-xs-perl/oldoldstable-security 4.030-1+deb11u1 amd64 [upgradable from: 4.030-1+b1]
libk5crypto3/oldoldstable-security 1.18.3-6+deb11u7 amd64 [upgradable from: 1.18.3-6+deb11u5]
libkrb5-3/oldoldstable-security 1.18.3-6+deb11u7 amd64 [upgradable from: 1.18.3-6+deb11u5]
libkrb5support0/oldoldstable-security 1.18.3-6+deb11u7 amd64 [upgradable from: 1.18.3-6+deb11u5]
libpam-modules-bin/oldoldstable-security 1.4.0-9+deb11u2 amd64 [upgradable from: 1.4.0-9+deb11u1]
libpam-modules/oldoldstable-security 1.4.0-9+deb11u2 amd64 [upgradable from: 1.4.0-9+deb11u1]
libpam-runtime/oldoldstable-security 1.4.0-9+deb11u2 all [upgradable from: 1.4.0-9+deb11u1]
libpam0g/oldoldstable-security 1.4.0-9+deb11u2 amd64 [upgradable from: 1.4.0-9+deb11u1]
libpve-guest-common-perl/stable 4.2-5 all [upgradable from: 4.2-4]
libpython3.9-minimal/oldoldstable-security 3.9.2-1+deb11u3 amd64 [upgradable from: 3.9.2-1+deb11u2]
libpython3.9-stdlib/oldoldstable-security 3.9.2-1+deb11u3 amd64 [upgradable from: 3.9.2-1+deb11u2]
libpython3.9/oldoldstable-security 3.9.2-1+deb11u3 amd64 [upgradable from: 3.9.2-1+deb11u2]
librabbitmq4/oldoldstable-security 0.10.0-1+deb11u1 amd64 [upgradable from: 0.10.0-1]
libsndfile1/oldoldstable-security 1.0.31-2+deb11u1 amd64 [upgradable from: 1.0.31-2]
libssl1.1/oldoldstable-security 1.1.1w-0+deb11u4 amd64 [upgradable from: 1.1.1w-0+deb11u2]
libtasn1-6/oldoldstable-security 4.16.0-2+deb11u2 amd64 [upgradable from: 4.16.0-2+deb11u1]
libunbound8/oldoldstable-security 1.13.1-1+deb11u5 amd64 [upgradable from: 1.13.1-1+deb11u4]
libxml2/oldoldstable-security 2.9.10+dfsg-6.7+deb11u9 amd64 [upgradable from: 2.9.10+dfsg-6.7+deb11u5]
libxslt1.1/oldoldstable-security 1.1.34-4+deb11u3 amd64 [upgradable from: 1.1.34-4+deb11u1]
locales/oldoldstable-security 2.31-13+deb11u13 all [upgradable from: 2.31-13+deb11u11]
login/oldoldstable-security 1:4.8.1-1+deb11u1 amd64 [upgradable from: 1:4.8.1-1]
openssh-client/oldoldstable-security 1:8.4p1-5+deb11u5 amd64 [upgradable from: 1:8.4p1-5+deb11u3]
openssh-server/oldoldstable-security 1:8.4p1-5+deb11u5 amd64 [upgradable from: 1:8.4p1-5+deb11u3]
openssh-sftp-server/oldoldstable-security 1:8.4p1-5+deb11u5 amd64 [upgradable from: 1:8.4p1-5+deb11u3]
openssl/oldoldstable-security 1.1.1w-0+deb11u4 amd64 [upgradable from: 1.1.1w-0+deb11u2]
passwd/oldoldstable-security 1:4.8.1-1+deb11u1 amd64 [upgradable from: 1:4.8.1-1]
proxmox-ve/stable 7.4-1 all [upgradable from: 7.3-1]
pve-kernel-helper/stable 7.3-8 all [upgradable from: 7.2-14]
pve-manager/stable 7.4-20 amd64 [upgradable from: 7.4-19]
python3-pkg-resources/oldoldstable-security 52.0.0-4+deb11u2 all [upgradable from: 52.0.0-4+deb11u1]
python3.9-minimal/oldoldstable-security 3.9.2-1+deb11u3 amd64 [upgradable from: 3.9.2-1+deb11u2]
python3.9/oldoldstable-security 3.9.2-1+deb11u3 amd64 [upgradable from: 3.9.2-1+deb11u2]
qemu-server/stable 7.4-7 amd64 [upgradable from: 7.4-6]
ssh/oldoldstable-security 1:8.4p1-5+deb11u5 all [upgradable from: 1:8.4p1-5+deb11u3]
tzdata/oldoldstable-security 2025b-0+deb11u1 all [upgradable from: 2024b-0+deb11u1]
uidmap/oldoldstable-security 1:4.8.1-1+deb11u1 amd64 [upgradable from: 1:4.8.1-1]
vim-common/oldoldstable-security 2:8.2.2434-3+deb11u3 all [upgradable from: 2:8.2.2434-3+deb11u1]
vim-tiny/oldoldstable-security 2:8.2.2434-3+deb11u3 amd64 [upgradable from: 2:8.2.2434-3+deb11u1]
wget/oldoldstable-security 1.21-1+deb11u2 amd64 [upgradable from: 1.21-1+deb11u1]
xsltproc/oldoldstable-security 1.1.34-4+deb11u3 amd64 [upgradable from: 1.1.34-4+deb11u1]
xxd/oldoldstable-security 2:8.2.2434-3+deb11u3 amd64 [upgradable from: 2:8.2.2434-3+deb11u1]Hi tayra,
Have you managed to solve it yet? (then mark the thread as solved)
The problem is your PVE version. You currently have version 7.1, but you need to update to version 7.4 before upgrade to version 8. You should install updates either from the WebGUI or in the shell using
If you have problem with updating please provide output of the
Upgrading to 7.4 is a prerequisite. Please read this guide: https://pve.proxmox.com/wiki/Upgrade_from_7_to_8
R.
Have you managed to solve it yet? (then mark the thread as solved)
The problem is your PVE version. You currently have version 7.1, but you need to update to version 7.4 before upgrade to version 8. You should install updates either from the WebGUI or in the shell using
apt update && apt upgradeIf you have problem with updating please provide output of the
apt update && apt upgrade command.Upgrading to 7.4 is a prerequisite. Please read this guide: https://pve.proxmox.com/wiki/Upgrade_from_7_to_8
R.
Hi,
Either use
Best regards,
No, never !or in the shell usingapt update && apt upgrade
Either use
apt full-upgrade or apt dist-upgrade Best regards,
Here's the reason why
apt upgrade is bad . I already suggested pveupdate && pveupgrade above. Giving them even more (and more advanced) options is probably not helpful.