I have been using VM for a while now, however, recently noticed that this VM isnt so undetectable afterall. Using pafish test shows that rdtsc vm exit calls are traced.
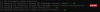
These are cpuid timing checks i believe.
Is it possible to hide these traces in proxmox?
Also i have found that someone managed to hide these traces by using configuration bellow:
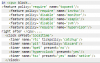
But this is libvirt xml configuration. How can i use these settings in Proxmox?

These are cpuid timing checks i believe.
Is it possible to hide these traces in proxmox?
Also i have found that someone managed to hide these traces by using configuration bellow:

But this is libvirt xml configuration. How can i use these settings in Proxmox?

