Im absolutely noob in both Proxmox and pfSense, but have fair experience with Unix/Debian through rPi.
Stumbled upon this while trying to search for a 5GB Router/Wifi and been researching for a month now.
I successfully managed to install Proxmox on a Dell Precision 3240 | Xeon 3.00GHz | 64GB RAM | Onboard 1GB NIC | Intel X520-DA2 on PCIe.
I added the X520 based on various advice to use fiber to keep heat low on the server.
As you can see I have 3 Network device : enp0s3166 (onboard 1GB) + enp1s0f0, enp1s0f1 (10G SFP+)
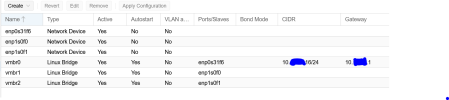
Currently Im able to access the Proxmox GUI on 10.10.10.16 as my gateway is 10.1.1.1
Im replacing my ISP with 5GB Fiber service. This is my current setup vis-a-vis future plan. My intention is to install pfSense, with vmbr1 as WAN and vmbr2 as LAN and
create a new network with gateway 10.100.100.1. I still havent connected the internet on the DA2, hence pfSense wont install (waiting for the Mikrotik switch + DAC)
Here is my /etc/network/interfaces content
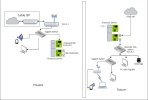
I need to access the Proxmox GUI from one of the desktops.
1. Is it as simple as plugging the PVE to the Gigabit switch and assign, say 10.100.100.16/24 with 10.100.100.1 gateway and call it a day? Or I need to make any more changes?
a. If so, then is it correct that I need to update the interfaces file from the console and restart?
2. If the pfSense is the gateway and for some reason it goes down, would I be able to still access the GUI from one of the desktops below?
Stumbled upon this while trying to search for a 5GB Router/Wifi and been researching for a month now.
I successfully managed to install Proxmox on a Dell Precision 3240 | Xeon 3.00GHz | 64GB RAM | Onboard 1GB NIC | Intel X520-DA2 on PCIe.
I added the X520 based on various advice to use fiber to keep heat low on the server.
As you can see I have 3 Network device : enp0s3166 (onboard 1GB) + enp1s0f0, enp1s0f1 (10G SFP+)

Currently Im able to access the Proxmox GUI on 10.10.10.16 as my gateway is 10.1.1.1
Im replacing my ISP with 5GB Fiber service. This is my current setup vis-a-vis future plan. My intention is to install pfSense, with vmbr1 as WAN and vmbr2 as LAN and
create a new network with gateway 10.100.100.1. I still havent connected the internet on the DA2, hence pfSense wont install (waiting for the Mikrotik switch + DAC)
Here is my /etc/network/interfaces content
Code:
auto lo
iface lo inet loopback
iface enp0s31f6 inet manual
iface enp1s0f0 inet manual
iface enp1s0f1 inet manual
auto vmbr0
iface vmbr0 inet static
address 10.10.10.16/24
gateway 10.10.10.1
bridge-ports enp0s31f6
bridge-stp off
bridge-fd 0
auto vmbr1
iface vmbr1 inet manual
bridge-ports enp1s0f0
bridge-stp off
bridge-fd 0
mtu 1500
auto vmbr2
iface vmbr2 inet manual
bridge-ports enp1s0f1
bridge-stp off
bridge-fd 0
I need to access the Proxmox GUI from one of the desktops.
1. Is it as simple as plugging the PVE to the Gigabit switch and assign, say 10.100.100.16/24 with 10.100.100.1 gateway and call it a day? Or I need to make any more changes?
a. If so, then is it correct that I need to update the interfaces file from the console and restart?
2. If the pfSense is the gateway and for some reason it goes down, would I be able to still access the GUI from one of the desktops below?

