Hi All,
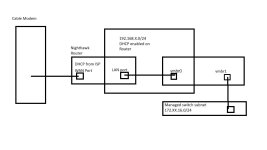
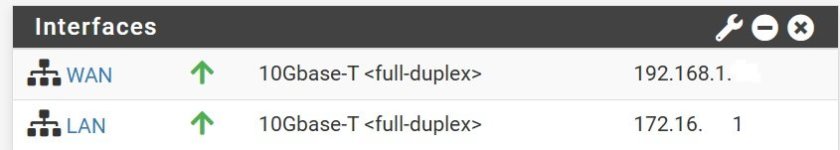
I'm very new to this so please don't beat me up too badly. I currently running pfsense in a VM on Proxmox sitting on a mini PC firewall appliance. I have made it far enough to have pfsense routing between my nighthawk router (192.168.x.0/24) and a private network space (172.16.xx.0/24) on a wired managed switch connected to the second physical interface on the appliance.
My next step is pretty much into the unknown. I want to replace my Nighthawk router and DHCP functionality with the appliance and run my Nighthawk in AP mode on a private LAN (either the existing one or I can create another subnet since the appliance has 4 physical ports.).
The two roadblock in the way for me are:
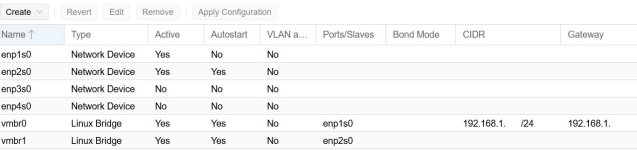
1. how to share a single IP on the WAN side with both proxmox and pfsense and still be able to get to the ProxMox web configurator. I "think" I need to create another bridge on vrmb0 which is the WAN port.
2. Eventually try to get VPN tunneling working on the pfsense with DHCP. I've read a bit about this and dynamic DNS is a topic that comes up.
I have attached some screenshots and a rudimentary drawing of my network that hopefully helps to make sense of it. I don't know how to set this up so both the proxmox IP and the pfsense IP are accessible on the private 172.16.xx.0/24 subnet while still connecting properly to the WAN .
I'm very new to this so please don't beat me up too badly. I currently running pfsense in a VM on Proxmox sitting on a mini PC firewall appliance. I have made it far enough to have pfsense routing between my nighthawk router (192.168.x.0/24) and a private network space (172.16.xx.0/24) on a wired managed switch connected to the second physical interface on the appliance.
My next step is pretty much into the unknown. I want to replace my Nighthawk router and DHCP functionality with the appliance and run my Nighthawk in AP mode on a private LAN (either the existing one or I can create another subnet since the appliance has 4 physical ports.).
The two roadblock in the way for me are:
1. how to share a single IP on the WAN side with both proxmox and pfsense and still be able to get to the ProxMox web configurator. I "think" I need to create another bridge on vrmb0 which is the WAN port.
2. Eventually try to get VPN tunneling working on the pfsense with DHCP. I've read a bit about this and dynamic DNS is a topic that comes up.
I have attached some screenshots and a rudimentary drawing of my network that hopefully helps to make sense of it. I don't know how to set this up so both the proxmox IP and the pfsense IP are accessible on the private 172.16.xx.0/24 subnet while still connecting properly to the WAN .