Hi all
I've had a search around and cant seem to find the answer. I basically want to know if I have correctly done blacklisting and if its working. I have an LSI sas card in my server which I am passing through to a VM so the VM can use the hard drive that is plugged into the SAS card. This seems to be working.
The bit I am concerned with is blacklisting. I want to ensure that this card is only ever used by that one VM and not by any other VMs or by proxmox itself.
In the following guide there are two methods for this (https://pve.proxmox.com/wiki/PCI(e)_Passthrough):
1 - Add the device ID to a new conf file at /etc/modprobe.d/somefile.conf
2 - Adding the drivername to the existing /etc/modprobe.d/pve-blacklist.conf
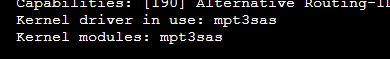
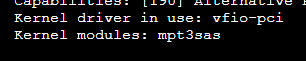
For option 2, I am not sure where to get the drivername so instead I did option 1. Using the follwoing command I find the device ID (in my case b6:00):
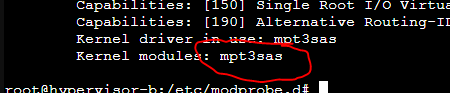
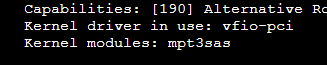
Then using the following command I find some other characters that are needed in the conf file:
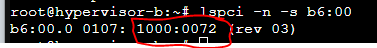
I then added the following into the new conf file:
After this I run
and reboot
So far so good but I would like to know if the blacklisting is working.
Is there an obvious way to test if blacklisting is working?
I've had a search around and cant seem to find the answer. I basically want to know if I have correctly done blacklisting and if its working. I have an LSI sas card in my server which I am passing through to a VM so the VM can use the hard drive that is plugged into the SAS card. This seems to be working.
The bit I am concerned with is blacklisting. I want to ensure that this card is only ever used by that one VM and not by any other VMs or by proxmox itself.
In the following guide there are two methods for this (https://pve.proxmox.com/wiki/PCI(e)_Passthrough):
1 - Add the device ID to a new conf file at /etc/modprobe.d/somefile.conf
2 - Adding the drivername to the existing /etc/modprobe.d/pve-blacklist.conf
For option 2, I am not sure where to get the drivername so instead I did option 1. Using the follwoing command I find the device ID (in my case b6:00):
Code:
lspci -v
Code:
lspci -n -s b6:00I then added the following into the new conf file:
Code:
options vfio-pci ids=1000:0072
update-initramfs -u -k all
and reboot
So far so good but I would like to know if the blacklisting is working.
Is there an obvious way to test if blacklisting is working?