Hello all,
i am running Proxmox (6.4-8) on Hetzner and installed an LXC (Ubuntu 20.04). I am facing problems with outgoing connections to some ports, for example to port 6000.
Everything is working fine from the pve-host, but it is not working from the LXC.
I tried from LXC:
Result from host:
All Firewalls on any level (datacenter, host, vm) are disabled.
this is my host network configuration:
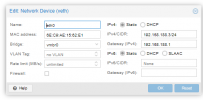
This is the configuration on my lxc:
Would love to have some feedback, thanks a lot.
i am running Proxmox (6.4-8) on Hetzner and installed an LXC (Ubuntu 20.04). I am facing problems with outgoing connections to some ports, for example to port 6000.
Everything is working fine from the pve-host, but it is not working from the LXC.
I tried from LXC:
nc -vz 84.139.123.XXX 6000
nc: connect to 84.139.123.XXX port 6000 (tcp) failed: Connection timed outnc -vz 84.139.123.XXX 5060
Connection to 84.139.123.XXX 5060 port [tcp/sip] succeeded!
nc -vz 84.139.123.XXX 443
Connection to 84.139.123.253 443 port [tcp/https] succeeded!nmap -p 6000 84.139.123.XXX
Starting Nmap 7.80 ( https://nmap.org ) at 2021-07-13 21:04 UTC
Nmap scan report for pXXX.dip0.t-ipconnect.de (84.139.123.XXX)
Host is up (0.034s latency).
PORT STATE SERVICE
6000/tcp filtered X11
Nmap done: 1 IP address (1 host up) scanned in 0.40 secondsResult from host:
root@pve ~ # nmap -p 6000 84.139.123.XXX
Starting Nmap 7.70 ( https://nmap.org ) at 2021-07-13 23:05 CEST
Nmap scan report for 84.139.123.XXX
Host is up (0.035s latency).
PORT STATE SERVICE
6000/tcp open X11
Nmap done: 1 IP address (1 host up) scanned in 17.17 secondsAll Firewalls on any level (datacenter, host, vm) are disabled.
this is my host network configuration:
### Hetzner Online GmbH installimage
source /etc/network/interfaces.d/*
auto lo
iface lo inet loopback
auto enp41s0
iface enp41s0 inet static
address 65.21.136.XXX
netmask 255.255.255.192
gateway 65.21.136.129
# route 65.21.136.128/26 via 65.21.136.129
up route add -net 65.21.136.128 netmask 255.255.255.192 gw 65.21.136.129 dev enp41s0
auto vmbr0
iface vmbr0 inet static
address 192.168.188.1
netmask 255.255.255.0
bridge_ports none
bridge_stp off
bridge_fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '192.168.188.0/24' -o enp41s0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.168.188.0/24' -o enp41s0 -j MASQUERADE
post-up iptables -t nat -A PREROUTING -i enp41s0 -p tcp --dport 6001 -j DNAT --to 192.168.188.3:6001
post-down iptables -t nat -D PREROUTING -i enp41s0 -p tcp --dport 6001 -j DNAT --to 192.168.188.3:6001
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 1
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 1This is the configuration on my lxc:

Would love to have some feedback, thanks a lot.

