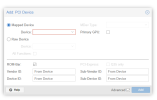
Never done SR-IOV myself but based on my readings and planning to do something similar for labbing ...
- begin with
THIS doc from Proxmox to enable it and (basic) instruction to pass-through
- AFAIK you enable all VF or not, then pass 1 VF to a VM, another VF to another VM, ... and leave the other VF "unused"
- if I correctly understand the VF are meant _solely_ for pass-through to VM and PVE uses the "Physical" function of the NIC for itself ...
- ... or is it first VF ?
- thus you could use all 4 "PF" of the T4 for PVE and 1 VF for each port for the OPN VM
- keep in mind that there is no virtual switch between the VF (from what I have read it is unsure there one in the 1 Gbps generation of Intel cards)
- so using VF for all VM's will isolate the trafic between them and force it to go through the switch each time and direction
- AFAIK using all VF distributed to different VM's is only used for lowering overhead for high networking needs between numerous (virtual) servers and clients located on other hardware
- for new VM type I tend to always go to Q35 except if something push me to 440FX (nothing currently)
- based on the above link (top of document) Q35 may be better because passing-through a device as a pure PCIe "Some guest applications benefit from this" although not describing if it is lower overhead, faster performance, removing some bottleneck if device is passed-through like a "really fast legacy PCIdevice".
If you only have 2 NIC's, the T2 and the T4, then yes moving the T2 to make a second host may be a fun or usefull project, depending of your willing. If you have the hardware on hand to make a second node I would recommend making the second node a test bench for SR-IOV before risking anything to your "prod" node, then move the NIC's, VM's, ... per you project plan.
Hope this helps !