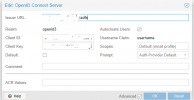
Hello!
Has anyone managed to configure openid logon with ADFS 2019 server? We've been banging our heads against the wall all day without success.
We got it work with Username Claim as "Default" but username is some weird long string with this option.
We would like to use "Username" or "Email" as claim but we got some error messages.
In ADFS server i have tried different kind of transform rules. I thought it would work with the "Send ldap attributes a Claims" rule template with outgoing claim type as email but no success.
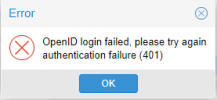
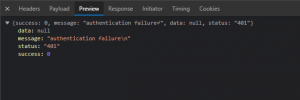
This wont work..
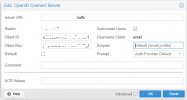
I wish someone had done this before. Thank you for your help in advance.
Best regards,
Mikko
Has anyone managed to configure openid logon with ADFS 2019 server? We've been banging our heads against the wall all day without success.
We got it work with Username Claim as "Default" but username is some weird long string with this option.
We would like to use "Username" or "Email" as claim but we got some error messages.
Code:
Jun 1 12:53:11 xxxxxxxxxx pvedaemon[2433391]: openid authentication failure; rhost=::ffff:10.25.21.53 msg=missing claim 'email'In ADFS server i have tried different kind of transform rules. I thought it would work with the "Send ldap attributes a Claims" rule template with outgoing claim type as email but no success.


This wont work..

I wish someone had done this before. Thank you for your help in advance.
Best regards,
Mikko
Attachments
Last edited: