Hello,
I have a few questions.
1. Is it explicitly neccessary to enable AES in the cpu flag settings when using kvm64?
2. Which AES versions are supported by that flag?
3. Would you advise to run an OPNsense using host cpu type or is it okay to run it as kvm64+aes?
EDIT:
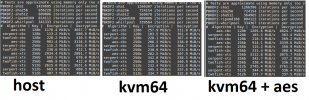
I did a quick test.
Question 1: The answer seems to be yes, can any of the devs please confirm this?
Question 3: I think there isn't really a difference. (Funny though that host was slower than kvm64+aes...)
I have a few questions.
1. Is it explicitly neccessary to enable AES in the cpu flag settings when using kvm64?
2. Which AES versions are supported by that flag?
3. Would you advise to run an OPNsense using host cpu type or is it okay to run it as kvm64+aes?
EDIT:
I did a quick test.
Question 1: The answer seems to be yes, can any of the devs please confirm this?
Question 3: I think there isn't really a difference. (Funny though that host was slower than kvm64+aes...)

Last edited:

