Hello,
I'm trying to setup minimal required permission to our everyday account. I would like to be able to launch or edit a sync job, but not allow deleting data from the data store. Seem like this is not possible ?
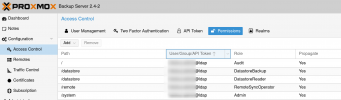
I tried to give theses permissions :
Seem like the permission DatastoreAdmin on /datastore is required to do what I want, but this also give access to file deletion I would like to avoid.
I'm trying to setup minimal required permission to our everyday account. I would like to be able to launch or edit a sync job, but not allow deleting data from the data store. Seem like this is not possible ?
I tried to give theses permissions :
Code:
acl:1:/:myuser@ldap:Audit
acl:1:/system:myuser@ldap:Admin
acl:1:/datastore:myuser@ldap:DatastoreReader
acl:1:/remote:myuser@ldap:RemoteSyncOperatorSeem like the permission DatastoreAdmin on /datastore is required to do what I want, but this also give access to file deletion I would like to avoid.