Hi,
I would like to migrate two NICs - i226-V (facing LAN) to OVS mainly due to RSTP functionality.
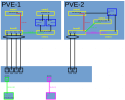
Bridge in question is vmbr23 and is used for all VMs including, OPNsense VM as interface to LAN. After applying changes - I use this as delayed fallback:
I loose connectivity to this server (no oob) and the only way is to restore linux bridge config. What also bothers me is that above command doesn't work well every time I use it. Sometimes doesn't copy back good config and just restarts host and I need to ask for local assistance (I work on it remotely); is there anything better to use for this purpose?
So, what's wrong or what am I missing?
Current linux bridge config:
I changed bridge vmbr23 (and its interfaces) to OVS without any RSTP options yet:
Logs:
EDIT:
Could this have been related to settings of lan's NIC and its tagging for native vlan? As this interface is used by OPNsense which doesn't tag that particular network segment? But also none of other vlans are reachable...
EDIT 2:
Adding rollback script, maybe will be useful for somebody:
I would like to migrate two NICs - i226-V (facing LAN) to OVS mainly due to RSTP functionality.
Bridge in question is vmbr23 and is used for all VMs including, OPNsense VM as interface to LAN. After applying changes - I use this as delayed fallback:
Code:
ifreload -a; (sleep 120; cp /etc/network/interfaces.bak /etc/network/interfaces && ifreload -a)& (sleep 240; reboot now)&I loose connectivity to this server (no oob) and the only way is to restore linux bridge config. What also bothers me is that above command doesn't work well every time I use it. Sometimes doesn't copy back good config and just restarts host and I need to ask for local assistance (I work on it remotely); is there anything better to use for this purpose?
So, what's wrong or what am I missing?
Current linux bridge config:
Code:
auto lo
iface lo inet loopback
iface enp2s0 inet manual
#lan
iface enp1s0 inet manual
#wan
iface enp3s0 inet manual
#iot
iface enp4s0 inet manual
#extra
auto vmbr23
iface vmbr23 inet manual
bridge-ports enp2s0 enp3s0.12
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
#LAN trunk i #3 IoT
auto vmbr4
iface vmbr4 inet static
address 10.10.0.2/26
bridge-ports enp4s0
bridge-stp off
bridge-fd 0
#extra
auto vmbr1
iface vmbr1 inet manual
bridge-ports enp1s0
bridge-stp off
bridge-fd 0
#WAN
auto vmbr23.1
iface vmbr23.1 inet static
address 172.16.0.11/24
gateway 172.16.0.1
#Główny dostęp
iface vmbr23.1 inet6 static
address 2001:XXXX
gateway 2001:XXXX
auto vmbr23.11
iface vmbr23.11 inet static
address 172.16.1.11/26
#storageI changed bridge vmbr23 (and its interfaces) to OVS without any RSTP options yet:
Code:
auto lo
iface lo inet loopback
auto enp2s0
iface enp2s0 inet manual
ovs_type OVSPort
ovs_bridge vmbr23
ovs_options tag=1 vlan_mode=native-untagged
#lan
iface enp1s0 inet manual
#wan
iface enp4s0 inet manual
#extra
auto enp3s0
iface enp3s0 inet manual
ovs_type OVSPort
ovs_bridge vmbr23
ovs_options tag=12
#iot
auto vlan1
iface vlan1 inet static
address 172.16.0.11/24
gateway 172.16.0.1
ovs_type OVSIntPort
ovs_bridge vmbr23
ovs_options tag=1
#main
auto vlan11
iface vlan11 inet static
address 172.16.1.11/26
ovs_type OVSIntPort
ovs_bridge vmbr23
ovs_options tag=11
#storage
auto vmbr4
iface vmbr4 inet static
address 10.10.0.2/26
bridge-ports enp4s0
bridge-stp off
bridge-fd 0
#extra
auto vmbr1
iface vmbr1 inet manual
bridge-ports enp1s0
bridge-stp off
bridge-fd 0
#WAN
auto vmbr23
iface vmbr23 inet manual
ovs_type OVSBridge
ovs_ports enp2s0 enp3s0 vlan1 vlan11
#LAN trunk #3 IoTLogs:
Code:
Apr 02 23:04:27 pvett ovs-vsctl[294882]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl -- --may-exist add-br vmbr23
Apr 02 23:04:27 pvett kernel: ovs-system: entered promiscuous mode
Apr 02 23:04:27 pvett kernel: No such timeout policy "ovs_test_tp"
Apr 02 23:04:27 pvett kernel: Failed to associated timeout policy `ovs_test_tp'
Apr 02 23:04:27 pvett ovs-vsctl[294928]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl -- --may-exist add-port vmbr23 enp2s0 -- --if-exists clear port enp2s0 bond_active_slave bond_mode cvlans external_ids lacp mac other_config qos tag trunks vlan_mode -- --if-exists clear interface enp2s0 mtu_request external-ids other_config options -- set Port enp2s0 tag=1 vlan_mode=native-untagged
Apr 02 23:04:27 pvett ovs-vsctl[294968]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl -- --may-exist add-port vmbr23 enp3s0 -- --if-exists clear port enp3s0 bond_active_slave bond_mode cvlans external_ids lacp mac other_config qos tag trunks vlan_mode -- --if-exists clear interface enp3s0 mtu_request external-ids other_config options -- set Port enp3s0 tag=12
Apr 02 23:04:27 pvett ovs-vsctl[295007]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl -- --may-exist add-port vmbr23 vlan1 -- --if-exists clear port vlan1 bond_active_slave bond_mode cvlans external_ids lacp mac other_config qos tag trunks vlan_mode -- --if-exists clear interface vlan1 mtu_request external-ids other_config options -- set Port vlan1 tag=1 -- set Interface vlan1 type=internal
Apr 02 23:04:27 pvett ovs-vsctl[295052]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl -- --may-exist add-port vmbr23 vlan11 -- --if-exists clear port vlan11 bond_active_slave bond_mode cvlans external_ids lacp mac other_config qos tag trunks vlan_mode -- --if-exists clear interface vlan11 mtu_request external-ids other_config options -- set Port vlan11 tag=11 -- set Interface vlan11 type=internalEDIT:
Could this have been related to settings of lan's NIC and its tagging for native vlan? As this interface is used by OPNsense which doesn't tag that particular network segment? But also none of other vlans are reachable...
Code:
auto enp2s0
iface enp2s0 inet manual
ovs_type OVSPort
ovs_bridge vmbr23
ovs_options tag=1 vlan_mode=native-untagged
#lanEDIT 2:
Adding rollback script, maybe will be useful for somebody:
Code:
#!/bin/bash
# Define backup file location, new interfaces file, and log file
BACKUP_FILE="/etc/network/interfaces.backup"
NEW_INTERFACES_FILE="/etc/network/interfaces.new"
LOG_FILE="/var/log/ifreload.log"
# Backup the current interfaces file
cp /etc/network/interfaces $BACKUP_FILE
# Copy the new interfaces file over the existing one
cp $NEW_INTERFACES_FILE /etc/network/interfaces
# Apply the network changes and write output to the log file
ifreload -a &>> $LOG_FILE
# Set a timeout for user confirmation (in seconds)
TIMEOUT=30
# Function to rollback changes and schedule a cancelable reboot
rollback() {
echo "Rolling back network changes..." &>> $LOG_FILE
cp $BACKUP_FILE /etc/network/interfaces
ifreload -a &>> $LOG_FILE
echo "Network changes have been reverted." &>> $LOG_FILE
# Schedule a reboot in 5 minutes
echo "Scheduling a reboot in 2 minutes. Run 'shutdown -c' to cancel." &>> $LOG_FILE
shutdown -r +2 &
# Wait for user input to cancel the reboot
read -t 60 -p "Press Enter within 1 minute to cancel the reboot: " cancel_reboot
if [ $? -eq 0 ]; then
# Cancel the scheduled reboot
shutdown -c
echo "Reboot canceled." &>> $LOG_FILE
else
echo "Reboot will proceed." &>> $LOG_FILE
fi
}
# Ask for user confirmation to keep the changes
read -t $TIMEOUT -p "Press Enter within $TIMEOUT seconds to confirm the changes: " confirmation
# Check if the user has provided confirmation
if [ $? -ne 0 ]; then
# No confirmation received, rollback and schedule a reboot
rollback
else
echo "Changes confirmed. No rollback needed." &>> $LOG_FILE
fi
Last edited: