Hello,
We have user request the Tenable Nessus test passed without any Critical,high and medium problem. we can see that there have one Vulnerabilities call 44135 - Web Server Generic Cookie Injection. May i know any thing we can do to fix the Vulnerabilities?
Synopsis
The remote web server is prone to a cookie injection attack.
Description
The remote host is running a web server that fails to adequately sanitize request strings of malicious
JavaScript. By leveraging this issue, an attacker may be able to inject arbitrary cookies. Depending on
the structure of the web application, it may be possible to launch a 'session fixation' attack using this
mechanism.
Please note that :
- Nessus did not check if the session fixation attack is feasible.
- This is not the only vector of session fixation.
See Also
https://en.wikipedia.org/wiki/Session_fixation
https://www.owasp.org/index.php/Session_Fixation
http://www.acros.si/papers/session_fixation.pdf
http://projects.webappsec.org/w/page/13246960/Session Fixation
Solution
Contact the vendor for a patch or upgrade.
Risk Factor
Medium
CVSS v2.0 Base Score
4.3 (CVSS2#AV:N/AC:M/Au:N/C:N/I /A:N)
/A:N)
Plugin Information
Published: 2010/01/25, Modified: 2022/04/11
Plugin Output
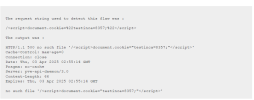
tcp/8006/www
We have user request the Tenable Nessus test passed without any Critical,high and medium problem. we can see that there have one Vulnerabilities call 44135 - Web Server Generic Cookie Injection. May i know any thing we can do to fix the Vulnerabilities?
Synopsis
The remote web server is prone to a cookie injection attack.
Description
The remote host is running a web server that fails to adequately sanitize request strings of malicious
JavaScript. By leveraging this issue, an attacker may be able to inject arbitrary cookies. Depending on
the structure of the web application, it may be possible to launch a 'session fixation' attack using this
mechanism.
Please note that :
- Nessus did not check if the session fixation attack is feasible.
- This is not the only vector of session fixation.
See Also
https://en.wikipedia.org/wiki/Session_fixation
https://www.owasp.org/index.php/Session_Fixation
http://www.acros.si/papers/session_fixation.pdf
http://projects.webappsec.org/w/page/13246960/Session Fixation
Solution
Contact the vendor for a patch or upgrade.
Risk Factor
Medium
CVSS v2.0 Base Score
4.3 (CVSS2#AV:N/AC:M/Au:N/C:N/I
Plugin Information
Published: 2010/01/25, Modified: 2022/04/11
Plugin Output
tcp/8006/www


