When I set up a backup task to push some VM and LXC backups to my test PBS server, I selected to enable client-side encryption. It made me acknowledge a warning and save a client-side encryption key.
Now, when I look at my PVE instance and the PBS server, neither of them show encryption is enabled for the backups in question. If I go to a VM and look at its Backup tab, it also says there is "No" encryption.
When I view Job Detail in Datacenter --> Backup, it doesn't say anything about whether the backup is encrypted, either way.
This seems … wrong? I'd understand the server not saying the backup is encrypted, as it's supposed to be encrypted before it leaves the PVE node, but shouldn't the PVE node or the PBS server acknowledge somewhere that the backups are encrypted?
Have I done something wrong?
Edit: Looks like it. I found the relevant docs here: https://pve.proxmox.com/pve-docs/pve-admin-guide.html#storage_pbs
From those, the
Mine does not. Fabulous. So, I need to start over, as there's no way to change that on an existing PBS storage.
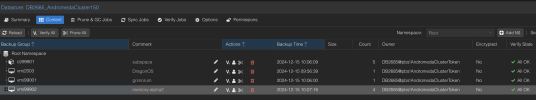
PBS Datastore:
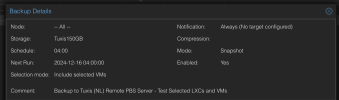
PVE Backup Job details:
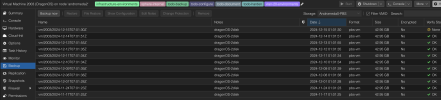
Here's an example VM:
Now, when I look at my PVE instance and the PBS server, neither of them show encryption is enabled for the backups in question. If I go to a VM and look at its Backup tab, it also says there is "No" encryption.
When I view Job Detail in Datacenter --> Backup, it doesn't say anything about whether the backup is encrypted, either way.
This seems … wrong? I'd understand the server not saying the backup is encrypted, as it's supposed to be encrypted before it leaves the PVE node, but shouldn't the PVE node or the PBS server acknowledge somewhere that the backups are encrypted?
Have I done something wrong?
Edit: Looks like it. I found the relevant docs here: https://pve.proxmox.com/pve-docs/pve-admin-guide.html#storage_pbs
From those, the
/etc/pve/storage.cfg entry for the PBS server should show an encryption key. Something like this:
Code:
pbs: backup
datastore main
server enya.proxmox.com
content backup
fingerprint 09:54:ef:..snip..:88:af:47:fe:4c:3b:cf:8b:26:88:0b:4e:3c:b2
prune-backups keep-all=1
username archiver@pbs
encryption-key a9:ee:c8:02:13:..snip..:2d:53:2c:98
master-pubkey 1Mine does not. Fabulous. So, I need to start over, as there's no way to change that on an existing PBS storage.
PBS Datastore:

PVE Backup Job details:

Here's an example VM:

Last edited:

