I have a Proxmox cluster, that uses LDAP to authenticate against a G Suite domain.
Previously, users were able to login successfully through their LDAP credentials.
However, recently I updated some packages (e.g. libpve-access-control) in order to try with the new LDAP sync feature (discussion thread).
Along the way, I've suddenly noticed that LDAP authentication seems to have broken. When users try to login via LDAP, they are getting:
Could this be related to the updated packages, or is it something else?
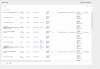
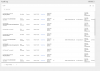
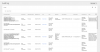
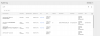
Here is my current /etc/pve/domains.cfg file:
In the audit logs for G Suite SecureLDAP, I see an error about:
(The username we're trying to sign in with here is "testvendor")
I assume the LDAP bind returning "NO_SUCH_OBJECT" might be the issue?
In /var/log/syslog, I see this:
Previously, users were able to login successfully through their LDAP credentials.
However, recently I updated some packages (e.g. libpve-access-control) in order to try with the new LDAP sync feature (discussion thread).
Along the way, I've suddenly noticed that LDAP authentication seems to have broken. When users try to login via LDAP, they are getting:
Code:
Login failed. Please try againCould this be related to the updated packages, or is it something else?
Here is my current /etc/pve/domains.cfg file:
Code:
# cat /etc/pve/domains.cfg
pam: pam
comment Linux PAM standard authentication
ldap: example.io
base_dn dc=example,dc=io
bind_dn uid=victorhooi,ou=Users,dc=example,dc=io
server1 ldap.google.com
user_attr uid
cert /etc/pve/priv/Google_2022_05_22_3494.crt
certkey /etc/pve/priv/Google_2022_05_22_3494.key
port 636
secure 1
verify 1
pve: pve
comment Proxmox VE authentication server
Code:
"LDAP bind with "" failed with NO_SUCH_OBJECT.":(The username we're trying to sign in with here is "testvendor")

I assume the LDAP bind returning "NO_SUCH_OBJECT" might be the issue?
In /var/log/syslog, I see this:
Code:
May 8 15:18:48 example-kvm01 pvedaemon[1714641]: authentication failure; rhost=127.0.0.1 user=testvendor@example.io msg=Invalid username at /usr/share/perl5/PVE/LDAP.pm line 83.