Hello hive mind, I've hit the limit of my google-foo and I'm in need of some assistance
I've got Proxmox 7.2 running on a R730, it was running on a single NIC for a while without issue but I recently had some time to work on networking a bit more and I've setup a second connection and teamed them, which has caused some issues. I have successfully setup LACP with trunking on this switch for my pfSense box without issue and the setup for the server is the same so I'm pretty sure this is a Proxmox configuration issue. Relevant sections of /etc/network/interfaces are shown below for reference.
Switch is setup with native VLAN 10 and tagged VLANs 5,20,30,40,50 on the ports for the server. Single or LACP the interfaces come up without issue on both ends regardless of configuraton.
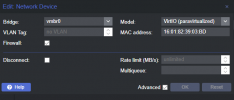
With the single NIC I have access to the host on the untagged VLAN 10 and I have VMs connected on tagged VLANs 5 and 20. In this configuration I do not have bridge-vlan-aware enabled.
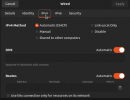
With the interfaces bonded but no other changes I lose the ability to communicate over the tagged VLANs used by the VMs. I am still able to communicate over the untagged native VLAN to the host and a VM that is also using the native VLAN.
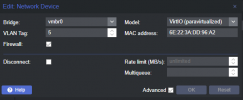
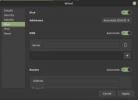
If I enable bridge-vlan-aware and setup interfaces for the tagged VLANs on the bridge I lose connectivity to the host and VMs.
What am I missing here? Why does a configuration that works on a single physical interface not work on a bonded logical interface? Additionally, why does everything break if I enable bridge-vlan-aware?
I've got Proxmox 7.2 running on a R730, it was running on a single NIC for a while without issue but I recently had some time to work on networking a bit more and I've setup a second connection and teamed them, which has caused some issues. I have successfully setup LACP with trunking on this switch for my pfSense box without issue and the setup for the server is the same so I'm pretty sure this is a Proxmox configuration issue. Relevant sections of /etc/network/interfaces are shown below for reference.
Switch is setup with native VLAN 10 and tagged VLANs 5,20,30,40,50 on the ports for the server. Single or LACP the interfaces come up without issue on both ends regardless of configuraton.
With the single NIC I have access to the host on the untagged VLAN 10 and I have VMs connected on tagged VLANs 5 and 20. In this configuration I do not have bridge-vlan-aware enabled.
With the interfaces bonded but no other changes I lose the ability to communicate over the tagged VLANs used by the VMs. I am still able to communicate over the untagged native VLAN to the host and a VM that is also using the native VLAN.
If I enable bridge-vlan-aware and setup interfaces for the tagged VLANs on the bridge I lose connectivity to the host and VMs.
What am I missing here? Why does a configuration that works on a single physical interface not work on a bonded logical interface? Additionally, why does everything break if I enable bridge-vlan-aware?
This works with the native/untagged VLAN and I'm able to use tagging on VM NICs
Code:
iface eno3 inet manual
auto vmbr0
iface vmbr0 inet static
address 192.168.10.210/24
gateway 192.168.10.1
bridge-ports eno3
bridge-stp off
bridge-fd 0Only the native/untagged vlan works when bonded. VM NICs with VLAN tags are unable to connect
Code:
iface eno3 inet manual
iface eno4 inet manual
auto bond0
iface bond0 inet manual
bond-slaves eno3 eno4
bond-miimon 100
bond-mode 802.3ad
bond-xmit-hash-policy layer2+3
auto vmbr0
iface vmbr0 inet static
address 192.168.10.210/24
gateway 192.168.10.1
bridge-ports bond0
bridge-stp off
bridge-fd 0No connectivity to host with this setup
Code:
iface eno3 inet manual
iface eno4 inet manual
auto bond0
iface bond0 inet manual
bond-slaves eno3 eno4
bond-miimon 100
bond-mode 802.3ad
bond-xmit-hash-policy layer2+3
auto vmbr0
iface vmbr0 inet static
address 192.168.10.210/24
gateway 192.168.10.1
bridge-ports bond0
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-pvid 10
bridge-vids 5,20,30,40,50
auto vmbr0.5
iface vmbr0.5 inet manual
auto vmbr0.20
iface vmbr0.20 inet manual
auto vmbr0.30
iface vmbr0.30 inet manual
auto vmbr0.40
iface vmbr0.40 inet manual
auto vmbr0.50
iface vmbr0.50 inet manual