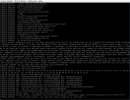
Every now and then my server kernel panic so I set up netconsole to see what's the culprit and it seems to be related to firewall(?)
Any idea how to fix that?
Here are the logs:
Pve version:
Any idea how to fix that?
Here are the logs:
Code:
[494221.511181] skbuff: skb_under_panic: text:00000000f0c6c75f len:74 put:14 head:000000001bebe299 data:000000007de59a6c tail:0x3c end:0xc0 dev:fwln7270i0
[494221.511181] skbuff: skb_under_panic: text:00000000f0c6c75f len:74 put:14 head:000000001bebe299 data:000000007de59a6c tail:0x3c end:0xc0 dev:fwln7270i0
[494221.511366] ------------[ cut here ]------------
[494221.511366] ------------[ cut here ]------------
[494221.511475] kernel BUG at net/core/skbuff.c:108!
[494221.511475] kernel BUG at net/core/skbuff.c:108!
[494221.511589] invalid opcode: 0000 [#1] SMP NOPTI
[494221.511589] invalid opcode: 0000 [#1] SMP NOPTI
[494221.511700] CPU: 11 PID: 0 Comm: swapper/11 Kdump: loaded Not tainted 5.4.128-1-pve #1
[494221.511700] CPU: 11 PID: 0 Comm: swapper/11 Kdump: loaded Not tainted 5.4.128-1-pve #1
[494221.511972] RIP: 0010:skb_panic+0x4c/0x4e
[494221.511972] RIP: 0010:skb_panic+0x4c/0x4e
[494221.512077] Code: 4f 70 50 8b 87 bc 00 00 00 50 8b 87 b8 00 00 00 50 ff b7 c8 00 00 00 4c 8b 8f c0 00 00 00 48 c7 c7 f8 25 83 8a e8 0f ba fb ff <0f> 0b 48 8b 55 08 48 c7 c1 a0 6d 55 8a e8 a2 ff ff ff 48 c7 c6 e0
[494221.512077] Code: 4f 70 50 8b 87 bc 00 00 00 50 8b 87 b8 00 00 00 50 ff b7 c8 00 00 00 4c 8b 8f c0 00 00 00 48 c7 c7 f8 25 83 8a e8 0f ba fb ff <0f> 0b 48 8b 55 08 48 c7 c1 a0 6d 55 8a e8 a2 ff ff ff 48 c7 c6 e0
[494221.512295] RSP: 0018:ffffa5ca40464780 EFLAGS: 00010246
[494221.512295] RSP: 0018:ffffa5ca40464780 EFLAGS: 00010246
[494221.512404] RAX: 000000000000008a RBX: ffff9ac6625b4858 RCX: 0000000000000000
[494221.512404] RAX: 000000000000008a RBX: ffff9ac6625b4858 RCX: 0000000000000000
[494221.512548] RDX: 0000000000000000 RSI: ffff9acc8ead78c8 RDI: ffff9acc8ead78c8
[494221.512548] RDX: 0000000000000000 RSI: ffff9acc8ead78c8 RDI: ffff9acc8ead78c8
[494221.512692] RBP: ffffa5ca404647a0 R08: 000000000000066c R09: 0000000000000a20
[494221.512692] RBP: ffffa5ca404647a0 R08: 000000000000066c R09: 0000000000000a20
[494221.512835] R10: 00000000000000c5 R11: 0000000000000000 R12: 000000000000003c
[494221.512835] R10: 00000000000000c5 R11: 0000000000000000 R12: 000000000000003c
[494221.512979] R13: ffff9acae7042000 R14: 00000000000086dd R15: ffff9ac6625b485e
[494221.512979] R13: ffff9acae7042000 R14: 00000000000086dd R15: ffff9ac6625b485e
[494221.513123] FS: 0000000000000000(0000) GS:ffff9acc8eac0000(0000) knlGS:0000000000000000
[494221.513123] FS: 0000000000000000(0000) GS:ffff9acc8eac0000(0000) knlGS:0000000000000000
[494221.513270] CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
[494221.513270] CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
[494221.513381] CR2: 0000008b9b930020 CR3: 0000001dde30e000 CR4: 0000000000340ee0
[494221.513381] CR2: 0000008b9b930020 CR3: 0000001dde30e000 CR4: 0000000000340ee0
[494221.513524] Call Trace:
[494221.513524] Call Trace:
[494221.513624] <IRQ>
[494221.513624] <IRQ>
[494221.513724] skb_push.cold.95+0x10/0x10
[494221.513724] skb_push.cold.95+0x10/0x10
[494221.513830] eth_header+0x2b/0xc0
[494221.513830] eth_header+0x2b/0xc0
[494221.513936] nf_send_reset6+0x2b3/0xb40 [nf_reject_ipv6]
[494221.513936] nf_send_reset6+0x2b3/0xb40 [nf_reject_ipv6]
[494221.514048] reject_tg6+0x91/0xd0 [ip6t_REJECT]
[494221.514048] reject_tg6+0x91/0xd0 [ip6t_REJECT]
[494221.514156] ip6t_do_table+0x2d8/0x6b0 [ip6_tables]
[494221.514156] ip6t_do_table+0x2d8/0x6b0 [ip6_tables]
[494221.514266] ip6table_filter_hook+0x1f/0x30 [ip6table_filter]
[494221.514266] ip6table_filter_hook+0x1f/0x30 [ip6table_filter]
[494221.514379] nf_hook_slow+0x49/0xd0
[494221.514379] nf_hook_slow+0x49/0xd0
[494221.514484] br_nf_forward_ip+0x20a/0x450
[494221.514484] br_nf_forward_ip+0x20a/0x450
[494221.514589] ? br_nf_hook_thresh+0xf0/0xf0
[494221.514589] ? br_nf_hook_thresh+0xf0/0xf0
[494221.514695] nf_hook_slow+0x49/0xd0
[494221.514695] nf_hook_slow+0x49/0xd0
[494221.514800] __br_forward+0xc2/0x1e0
[494221.514800] __br_forward+0xc2/0x1e0
[494221.514904] ? br_dev_queue_push_xmit+0x1a0/0x1a0
[494221.514904] ? br_dev_queue_push_xmit+0x1a0/0x1a0
[494221.515012] br_forward+0xcc/0xe0
[494221.515012] br_forward+0xcc/0xe0
[494221.515114] br_handle_frame_finish+0x2d5/0x440
[494221.515114] br_handle_frame_finish+0x2d5/0x440
[494221.515222] ? br_pass_frame_up+0x150/0x150
[494221.515222] ? br_pass_frame_up+0x150/0x150
[494221.515329] br_nf_hook_thresh+0xda/0xf0
[494221.515329] br_nf_hook_thresh+0xda/0xf0
[494221.515434] ? br_pass_frame_up+0x150/0x150
[494221.515434] ? br_pass_frame_up+0x150/0x150
[494221.515540] br_nf_pre_routing_finish_ipv6+0x140/0x200
[494221.515540] br_nf_pre_routing_finish_ipv6+0x140/0x200
[494221.515649] ? br_pass_frame_up+0x150/0x150
[494221.515649] ? br_pass_frame_up+0x150/0x150
[494221.515755] ? nf_hook_slow+0x49/0xd0
[494221.515755] ? nf_hook_slow+0x49/0xd0
[494221.515858] br_nf_pre_routing_ipv6+0x174/0x190
[494221.515858] br_nf_pre_routing_ipv6+0x174/0x190
[494221.515966] ? br_nf_pre_routing+0x4e0/0x4e0
[494221.515966] ? br_nf_pre_routing+0x4e0/0x4e0
[494221.516072] br_nf_pre_routing+0x3c4/0x4e0
[494221.516072] br_nf_pre_routing+0x3c4/0x4e0
[494221.516180] ? ip6_rcv_finish_core.isra.22+0xc0/0xc0
[494221.516180] ? ip6_rcv_finish_core.isra.22+0xc0/0xc0
[494221.516289] br_handle_frame+0x1c4/0x370
[494221.516289] br_handle_frame+0x1c4/0x370
[494221.516393] ? br_pass_frame_up+0x150/0x150
[494221.516393] ? br_pass_frame_up+0x150/0x150
[494221.516500] __netif_receive_skb_core+0x3a0/0xc50
[494221.516500] __netif_receive_skb_core+0x3a0/0xc50
[494221.516609] ? netif_receive_skb_list_internal+0x188/0x290
[494221.516609] ? netif_receive_skb_list_internal+0x188/0x290
[494221.516719] __netif_receive_skb_one_core+0x3e/0xa0
[494221.516719] __netif_receive_skb_one_core+0x3e/0xa0
[494221.516827] __netif_receive_skb+0x18/0x60
[494221.516827] __netif_receive_skb+0x18/0x60
[494221.516933] process_backlog+0xb8/0x170
[494221.516933] process_backlog+0xb8/0x170
[494221.517037] net_rx_action+0x138/0x380
[494221.517037] net_rx_action+0x138/0x380
[494221.517143] __do_softirq+0xdc/0x2d4
[494221.517143] __do_softirq+0xdc/0x2d4
[494221.517248] irq_exit+0xa9/0xb0
[494221.517248] irq_exit+0xa9/0xb0
[494221.517350] do_IRQ+0x59/0xe0
[494221.517350] do_IRQ+0x59/0xe0
[494221.517452] common_interrupt+0xf/0xf
[494221.517452] common_interrupt+0xf/0xf
[494221.517555] </IRQ>
[494221.517555] </IRQ>
[494221.517655] RIP: 0010:cpuidle_enter_state+0xbd/0x450
[494221.517655] RIP: 0010:cpuidle_enter_state+0xbd/0x450
[494221.517763] Code: ff e8 47 66 88 ff 80 7d c7 00 74 17 9c 58 0f 1f 44 00 00 f6 c4 02 0f 85 63 03 00 00 31 ff e8 7a 72 8e ff fb 66 0f 1f 44 00 00 <45> 85 ed 0f 88 8d 02 00 00 49 63 cd 48 8b 75 d0 48 2b 75 c8 48 8d
[494221.517763] Code: ff e8 47 66 88 ff 80 7d c7 00 74 17 9c 58 0f 1f 44 00 00 f6 c4 02 0f 85 63 03 00 00 31 ff e8 7a 72 8e ff fb 66 0f 1f 44 00 00 <45> 85 ed 0f 88 8d 02 00 00 49 63 cd 48 8b 75 d0 48 2b 75 c8 48 8d
[494221.517976] RSP: 0018:ffffa5ca4017fe48 EFLAGS: 00000246 ORIG_RAX: ffffffffffffffdb
[494221.517976] RSP: 0018:ffffa5ca4017fe48 EFLAGS: 00000246 ORIG_RAX: ffffffffffffffdb
[494221.518122] RAX: ffff9acc8eaeae00 RBX: ffffffff8ab66a00 RCX: 000000000000001f
[494221.518122] RAX: ffff9acc8eaeae00 RBX: ffffffff8ab66a00 RCX: 000000000000001f
[494221.518265] RDX: 0001c17de99c46d2 RSI: 00000000295e2e4e RDI: 0000000000000000
[494221.518265] RDX: 0001c17de99c46d2 RSI: 00000000295e2e4e RDI: 0000000000000000
[494221.518408] RBP: ffffa5ca4017fe88 R08: 0000000000000002 R09: 000000000002a680
[494221.518408] RBP: ffffa5ca4017fe88 R08: 0000000000000002 R09: 000000000002a680
[494221.518552] R10: 00056efffe2a4e29 R11: ffff9acc8eae9aa0 R12: ffff9acc791d0c00
[494221.518552] R10: 00056efffe2a4e29 R11: ffff9acc8eae9aa0 R12: ffff9acc791d0c00
[494221.518696] R13: 0000000000000002 R14: ffffffff8ab66ad8 R15: ffffffff8ab66ac0
[494221.518696] R13: 0000000000000002 R14: ffffffff8ab66ad8 R15: ffffffff8ab66ac0
[494221.518843] ? cpuidle_enter_state+0x99/0x450
[494221.518843] ? cpuidle_enter_state+0x99/0x450
[494221.518953] cpuidle_enter+0x2e/0x40
[494221.518953] cpuidle_enter+0x2e/0x40
[494221.519059] call_cpuidle+0x23/0x40
[494221.519059] call_cpuidle+0x23/0x40
[494221.519165] do_idle+0x22c/0x270
[494221.519165] do_idle+0x22c/0x270
[494221.519270] cpu_startup_entry+0x1d/0x20
[494221.519270] cpu_startup_entry+0x1d/0x20
[494221.519378] start_secondary+0x166/0x1c0
[494221.519378] start_secondary+0x166/0x1c0
[494221.519487] secondary_startup_64+0xa4/0xb0
[494221.519487] secondary_startup_64+0xa4/0xb0Pve version:
proxmox-ve: 6.4-1 (running kernel: 5.4.128-1-pve)
pve-manager: 6.4-13 (running version: 6.4-13/9f411e79)
pve-kernel-5.4: 6.4-5
pve-kernel-helper: 6.4-5
pve-kernel-5.4.128-1-pve: 5.4.128-1
pve-kernel-5.4.119-1-pve: 5.4.119-1
ceph-fuse: 12.2.11+dfsg1-2.1+b1
corosync: 3.1.2-pve1
criu: 3.11-3
glusterfs-client: 5.5-3
ifupdown: 0.8.35+pve1
ksmtuned: 4.20150325+b1
libjs-extjs: 6.0.1-10
libknet1: 1.20-pve1
libproxmox-acme-perl: 1.1.0
libproxmox-backup-qemu0: 1.1.0-1
libpve-access-control: 6.4-3
libpve-apiclient-perl: 3.1-3
libpve-common-perl: 6.4-3
libpve-guest-common-perl: 3.1-5
libpve-http-server-perl: 3.2-3
libpve-storage-perl: 6.4-1
libqb0: 1.0.5-1
libspice-server1: 0.14.2-4~pve6+1
lvm2: 2.03.02-pve4
lxc-pve: 4.0.6-2
lxcfs: 4.0.6-pve1
novnc-pve: 1.1.0-1
proxmox-backup-client: 1.1.12-1
proxmox-mini-journalreader: 1.1-1
proxmox-widget-toolkit: 2.6-1
pve-cluster: 6.4-1
pve-container: 3.3-6
pve-docs: 6.4-2
pve-edk2-firmware: 2.20200531-1
pve-firewall: 4.1-4
pve-firmware: 3.2-4
pve-ha-manager: 3.1-1
pve-i18n: 2.3-1
pve-qemu-kvm: 5.2.0-6
pve-xtermjs: 4.7.0-3
qemu-server: 6.4-2
smartmontools: 7.2-pve2
spiceterm: 3.1-1
vncterm: 1.6-2
pve-manager: 6.4-13 (running version: 6.4-13/9f411e79)
pve-kernel-5.4: 6.4-5
pve-kernel-helper: 6.4-5
pve-kernel-5.4.128-1-pve: 5.4.128-1
pve-kernel-5.4.119-1-pve: 5.4.119-1
ceph-fuse: 12.2.11+dfsg1-2.1+b1
corosync: 3.1.2-pve1
criu: 3.11-3
glusterfs-client: 5.5-3
ifupdown: 0.8.35+pve1
ksmtuned: 4.20150325+b1
libjs-extjs: 6.0.1-10
libknet1: 1.20-pve1
libproxmox-acme-perl: 1.1.0
libproxmox-backup-qemu0: 1.1.0-1
libpve-access-control: 6.4-3
libpve-apiclient-perl: 3.1-3
libpve-common-perl: 6.4-3
libpve-guest-common-perl: 3.1-5
libpve-http-server-perl: 3.2-3
libpve-storage-perl: 6.4-1
libqb0: 1.0.5-1
libspice-server1: 0.14.2-4~pve6+1
lvm2: 2.03.02-pve4
lxc-pve: 4.0.6-2
lxcfs: 4.0.6-pve1
novnc-pve: 1.1.0-1
proxmox-backup-client: 1.1.12-1
proxmox-mini-journalreader: 1.1-1
proxmox-widget-toolkit: 2.6-1
pve-cluster: 6.4-1
pve-container: 3.3-6
pve-docs: 6.4-2
pve-edk2-firmware: 2.20200531-1
pve-firewall: 4.1-4
pve-firmware: 3.2-4
pve-ha-manager: 3.1-1
pve-i18n: 2.3-1
pve-qemu-kvm: 5.2.0-6
pve-xtermjs: 4.7.0-3
qemu-server: 6.4-2
smartmontools: 7.2-pve2
spiceterm: 3.1-1
vncterm: 1.6-2