Hi guys,
I currently have my Proxmox running on an Intel NUC with just 1 NIC, and I would like to isolate some VM/LXC for learning purposes.
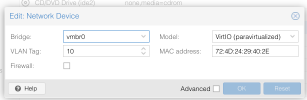
I have a OPNsense firewall setup with the following configuration, which is used to route all traffic from my VE:
How should I achieve this?
I achived something by applying firewall rules in the same 10.0.92.0 network, but this is not ideal. I am so new at networking, so any help or any ideas/explanations will be so appreciated.
Thank you in advance
I currently have my Proxmox running on an Intel NUC with just 1 NIC, and I would like to isolate some VM/LXC for learning purposes.
I have a OPNsense firewall setup with the following configuration, which is used to route all traffic from my VE:
- WAN interface: 192.168.1.10
- LAN interface: 10.0.92.1
How should I achieve this?
I achived something by applying firewall rules in the same 10.0.92.0 network, but this is not ideal. I am so new at networking, so any help or any ideas/explanations will be so appreciated.
Thank you in advance
Last edited: