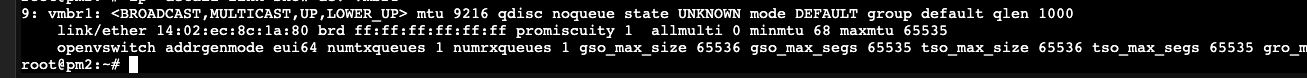
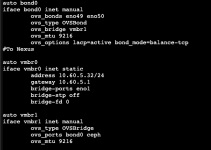
IDS on VM , cant see alla traffic only BUM and dst to self mac
- Thread starter PmUserZFS
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
You have to enable promiscous mode on the bridge too. The guest does not control promiscuous mode on the host.
https://docs.openvswitch.org/en/latest/faq/configuration/
https://docs.openvswitch.org/en/latest/faq/configuration/
Since there is a complete lack of SPAN/Mirror examples using Linux Bridges into Security Onion, I thought I'd post what got working.... Also is an example using multiple bridge mirrors, which is discussed but never actually shown anywhere.
Disclaimer, I am still in the very early stages of setting up a home security lab. So, I may eventually switch to OVS like everyone else, but I didn't want to redo my whole network configuration and I honestly hate the CLI syntax of OVS. I've been using Proxmox for about 2 weeks. So, there are random IDK, correct me if I am wrong parts, but I would...
Disclaimer, I am still in the very early stages of setting up a home security lab. So, I may eventually switch to OVS like everyone else, but I didn't want to redo my whole network configuration and I honestly hate the CLI syntax of OVS. I've been using Proxmox for about 2 weeks. So, there are random IDK, correct me if I am wrong parts, but I would...
- JD-Howard
- guide mirroring promiscious mode security onion span ports tap traffic controll
- Replies: 8
- Forum: Proxmox VE: Networking and Firewall
Last edited:
Hi, yes OVS is prom by default, and tou can see that on my suppiled screenshot of vmbr1, prom=1You have to enable promiscous mode on the bridge too. The guest does not control promiscuous mode on the host.
https://docs.openvswitch.org/en/latest/faq/configuration/
Since there is a complete lack of SPAN/Mirror examples using Linux Bridges into Security Onion, I thought I'd post what got working.... Also is an example using multiple bridge mirrors, which is discussed but never actually shown anywhere.
Disclaimer, I am still in the very early stages of setting up a home security lab. So, I may eventually switch to OVS like everyone else, but I didn't want to redo my whole network configuration and I honestly hate the CLI syntax of OVS. I've been using Proxmox for about 2 weeks. So, there are random IDK, correct me if I am wrong parts, but I would...
- JD-Howard
- guide mirroring promiscious mode security onion span ports tap traffic controll
- Replies: 8
- Forum: Proxmox VE: Networking and Firewall
The tap interface on the host is already set to promiscuous, but the bridge won't forward all packets to that port (only according to the fdb of the bridge). Setting the bridge itself to promiscuous won't help either since then only the host will receive all packets from that bridge.
You need to either use OVS and define a SPAN port [1] there or use the tc solution linked in the previous post. Both methods will require you to have a IDS VM running on each host, since it only works for traffic on that local bridge - not in the whole network. There's some discussion about implementing port mirroring (locally or even across multiple nodes) going on here [2], if you want to chime in.
[1] https://docs.openvswitch.org/en/latest/faq/configuration/
[2] https://bugzilla.proxmox.com/show_bug.cgi?id=6150
You need to either use OVS and define a SPAN port [1] there or use the tc solution linked in the previous post. Both methods will require you to have a IDS VM running on each host, since it only works for traffic on that local bridge - not in the whole network. There's some discussion about implementing port mirroring (locally or even across multiple nodes) going on here [2], if you want to chime in.
[1] https://docs.openvswitch.org/en/latest/faq/configuration/
[2] https://bugzilla.proxmox.com/show_bug.cgi?id=6150
ah, thnx! Ill look into the span thingThe tap interface on the host is already set to promiscuous, but the bridge won't forward all packets to that port (only according to the fdb of the bridge). Setting the bridge itself to promiscuous won't help either since then only the host will receive all packets from that bridge.
You need to either use OVS and define a SPAN port [1] there or use the tc solution linked in the previous post. Both methods will require you to have a IDS VM running on each host, since it only works for traffic on that local bridge - not in the whole network. There's some discussion about implementing port mirroring (locally or even across multiple nodes) going on here [2], if you want to chime in.
[1] https://docs.openvswitch.org/en/latest/faq/configuration/
[2] https://bugzilla.proxmox.com/show_bug.cgi?id=6150