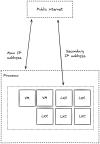
Hello, I have the following scenario. I installed Proxmox on my bare metal server and I later ordered an additional IPv4 /32 address. I want to access and perform network operations on the PVE host with the main IP address only, and use the secondary IP address strictly for my VM's and LXC containers. I've only ever setup NAT masquerading with a single IP address but never more than 1.
- I have 1 NIC
- How do I add the 2nd IP address to Proxmox?
- Is routed or NAT masquerading the appropriate method here?
Both addresses are in the same subnet. I've tried adding a new bridge for the 2nd address in the web ui but I get the following: "gateway: Default gateway already exists on interface 'vmbr0'."
- I have 1 NIC
- How do I add the 2nd IP address to Proxmox?
- Is routed or NAT masquerading the appropriate method here?
Both addresses are in the same subnet. I've tried adding a new bridge for the 2nd address in the web ui but I get the following: "gateway: Default gateway already exists on interface 'vmbr0'."

Last edited:

