Hello,
i currently have the following environment:
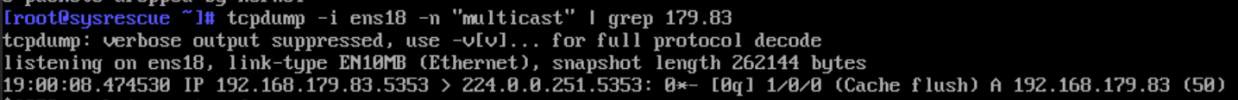
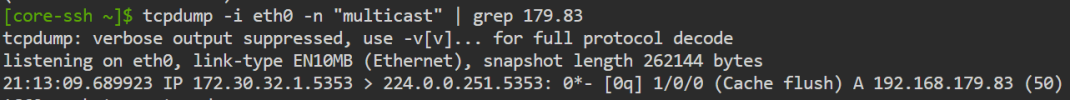
I did some research and was stumbling over mDNS, IGMP snooping etc... Also found this exact guide: https://www.home-assistant.io/integrations/zeroconf/#libvirt-virtual-machine-with-macvtap-adapter
I think that i need to enable "something" on the Proxmox node to allow multicast, but i'm not able to find the correct way of enabling this.
Using the OpenvSwitch is not crucial, i could switch to a Linux bridge, if this helps me any further.
i currently have the following environment:
- IKEA Dirigera Hub, which is HomeKit capable
- FRITZ!Box 7590 AX
- Proxmox single node, running a Home Assistant VM
- vmbr0 as a OpenvSwitch Bridge
I did some research and was stumbling over mDNS, IGMP snooping etc... Also found this exact guide: https://www.home-assistant.io/integrations/zeroconf/#libvirt-virtual-machine-with-macvtap-adapter
I think that i need to enable "something" on the Proxmox node to allow multicast, but i'm not able to find the correct way of enabling this.
Using the OpenvSwitch is not crucial, i could switch to a Linux bridge, if this helps me any further.
Last edited: