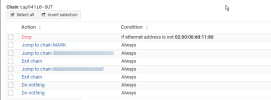
Hi, we've never used pve-firewall and now trying to consider it for a server.
This is an OVH installation so we have a host IP and additional ones assigned to a KVM.
I did some testing but none of the rules applied to the KVM itself seemed to work. At the host level they worked but only after a restart.
So my questions, to confirm we can use it or not are:
- can I have it activated at a KVM or CT level only? By that I mean, firewall running without rules on the host.
- in this case would the fact of having an iptables ruling firewall at the host level (or KVM) affect or make it unusable?
- should the rules be active straight away after inserting them via web UI or does some service/network need to be restarted?
- are there any tools/commands to... say update dynamic IPs via a cron from the command lines?
Thanks for any help.
This is an OVH installation so we have a host IP and additional ones assigned to a KVM.
I did some testing but none of the rules applied to the KVM itself seemed to work. At the host level they worked but only after a restart.
So my questions, to confirm we can use it or not are:
- can I have it activated at a KVM or CT level only? By that I mean, firewall running without rules on the host.
- in this case would the fact of having an iptables ruling firewall at the host level (or KVM) affect or make it unusable?
- should the rules be active straight away after inserting them via web UI or does some service/network need to be restarted?
- are there any tools/commands to... say update dynamic IPs via a cron from the command lines?
Thanks for any help.